Spyware, ransomware and cryptojacking malware have been increasingly detected on industrial control system (ICS) computers, according to data collected in the first half of 2022 by cybersecurity firm Kaspersky.
The data comes from ICS-related Windows devices protected by Kaspersky products, including HMIs, SCADA systems, historians, data gateways, engineering workstations, computers used for the administration of industrial networks, and devices used to develop software for industrial systems.
In the first half of 2022, Kaspersky products blocked malicious objects on nearly 32% of protected ICS devices, which is roughly the same as in the two previous years.
However, the total number of malware families exceeded 7,200 — this number was at approximately 5,000 in the past two years.
The most significant increase, roughly 3 percentage points, was seen for malicious scripts and phishing pages, as well as malicious documents.
According to Kaspersky data, the percentage of devices on which spyware was blocked has been steadily increasing since the first half of 2020. Spyware in this case includes trojans, backdoors and keyloggers.
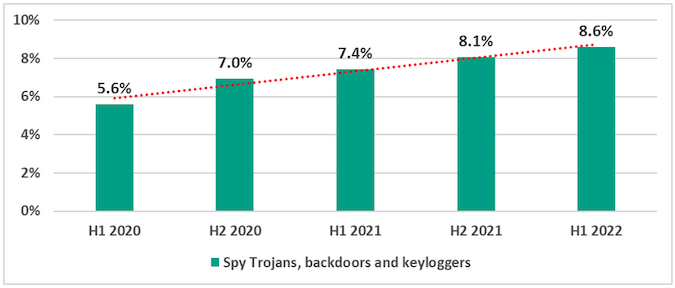
A steady increase has also been seen in cryptojacking malware, with malicious cryptocurrency miners that run in web browsers being spotted on 1.8% of devices and miners in the form of executables seen on 2.3% of devices.
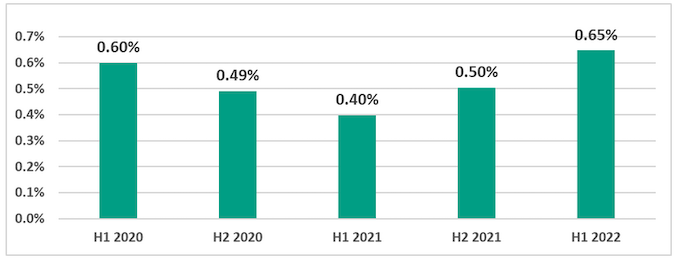
Ransomware was blocked on 0.65% of ICS computers, which represents the highest percentage for the past years and a significant increase from the first half of 2021. February 2022 was the month with the highest number of ransomware detections for the past two and a half years.
A regional breakdown of the data shows that the most significant growth of malware detection was in the Middle East and Latin America.
As for the most targeted industries, building automation and oil and gas are at the top with 42.2% and 39.6%, respectively.
Building automation systems can be a tempting target for malicious actors as they can be leveraged to access more valuable devices. Kaspersky reported recently that a China-linked threat group had used such systems as the point of entry into a telecoms company.
Additional information on the industrial automation threat landscape in H1 2022 can be found in Kaspersky’s full report.
Related: Kaspersky Sees Rise in Ransomware Attacks on ICS Devices in Developed Countries
Related: Belarus, Ukraine Saw Largest Increase in ICS Attacks During H1 2021
Related: Nearly Half of ICS Devices Protected by Kaspersky Targeted in 2018
















