A shocking 87 percent of the victims in a study of data breaches jointly conducted by Verizon and the U.S. Secret Service had evidence of the breach in their log files, yet missed it. According to the 2010 Verizon Data Breach Investigations Report, 60 percent of breaches were discovered by external parties, and then only after a considerable amount of time.
Most breaches were considered avoidable if security basics had been followed Only 4 percent of breaches assessed required difficult and expensive protective measures.
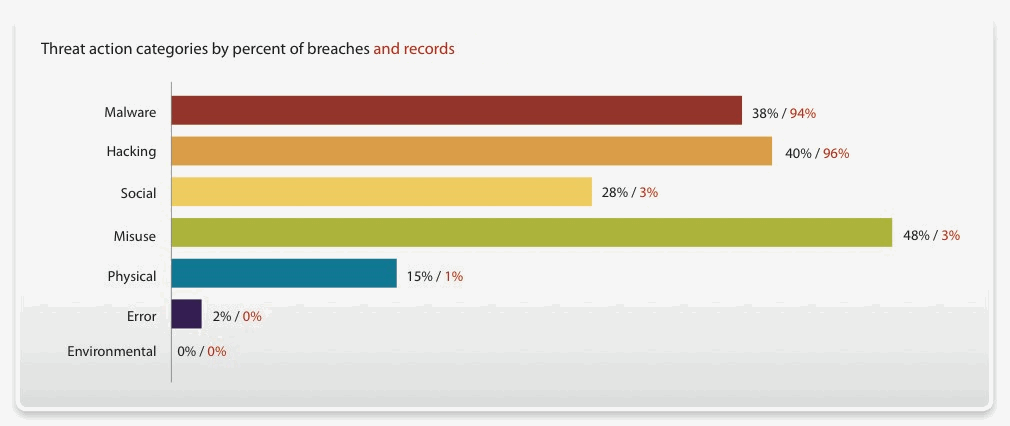
The new report covers 900-plus breaches involving more than 900 million compromised records. Some of the key findings: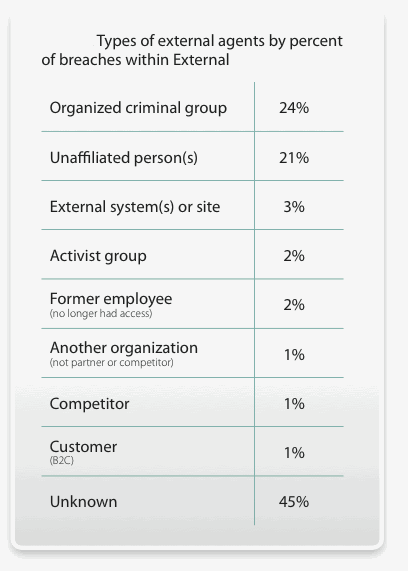
• Most data breaches investigated were caused by external sources. Sixty-nine percent of breaches resulted from these sources.
• Many breaches involved privilege misuse. Forty-eight percent of breaches were attributed to users who, for malicious purposes, abused their right to access corporate information.
• As in previous years, nearly all data was breached from servers and online applications.
• Meeting PCI-DSS compliance continues to be critically important. Seventy-nine percent of victims subject to the PCI-DSS standard hadn’t achieved compliance prior to the breach.
Financial services, hospitality and retail still comprise the “Big Three” of industries affected (33 percent, 23 percent and 15 percent, respectively).
Strict Security Crucial
The report recommends strict adherence to basic security procedures as the key to avoiding daa breaches. These procedures include:
• Restricting and monitoring privileged users. The data from the Secret Service showed that there were more insider breaches than ever before. According to the report, the best preventive strategies for controlling insiders are pre-employment screening, limits on user privileges and separation of duties. Privileged use should be logged and messages detailing activity generated for management.
• Attention to “minor” policy violations. The study finds a correlation between seemingly minor policy violations and more serious abuse. Based on case data, the presence of illegal content on user systems or other inappropriate behavior is a reasonable indicator of a future breach. Actively searching for such indicators is recommended.
• Prevention of credential theft. Keeping credential-capturing malware off systems should priority No. 1. Two-factor authentication is recommended where appropriate.
• Monitoring and filtering outbound traffic. In many breaches, something (data, communications, connections) goes out externally via an organization’s network which, if prevented, could break the chain and stop the breach.
• Improving event monitoring and log analysis. Almost all victims of a breach have evidence of that breach in their logs. Ensuring that there are adequate resources to monitor these logs carefully reduces the risk of breach.