Qualys today announced the release of the second annual “Top Cyber Security Risks Report.” featuring new data from HP TippingPoint DVLabs, SANS Institute and Qualys Research Labs, plus a “deep dive” analysis of PDF attacks, one of the fastest-growing classes of exploits now in play.
Qualys’s data on patching status for vulnerabilities alone is derived from more than 13 million scans each week.
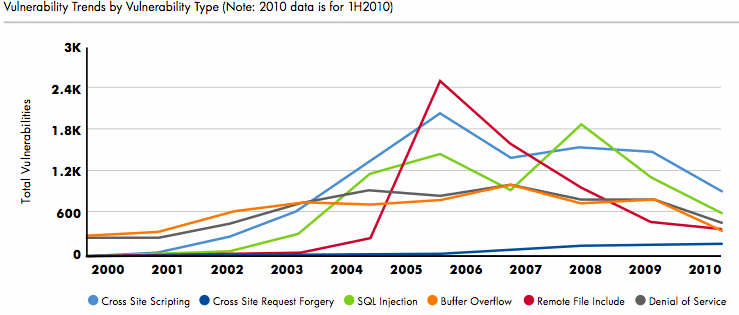
The report contains no major surprises, but rather documents in a thorough manner many of the trends that have been cited in the technical press over the past two years.
• Enterprise computing is becoming increasingly “consumerized.” Some of the most serious security issues this year have stemmed from increased use of consumer technologies in the enterprise, including downloads of applications and use of social media tools on company computers.
• Attacks on web applications have substantially increased, while conventional attacks against operating systems continue to decline. Once exception to this decline is the rise of cross site request forgeries.
• Servers are by far the preferred targets of attack. Attacks against servers outnumber those against clients 50 to 1.
• The sophistication of attacks has increased across all attack types, including malicious JavaScript as well as server-side attacks like PHP file attacks.
• Legacy threats linger. Well-known and documented malware such as SQL Slammer is still prevalent.
• The number of unpatched vulnerabilities has increased dramatically, and now often runs into the hundreds per product.
The report details the sophistication of many new attacks. One example is a technique that involves the loading of a number of innocuous JavaScript fragments into a site. None of them are malicious in themselves, but when all are loaded, they assemble themselves into a malicious entity. In its typically under-stated tone, the report concludes that “simple pattern, or signature-based, detection techniques commonly associated with anti-virus solutions, will no longer be effective on their own.”
In addition to statistics and summaries of trends, the report also contains an in-depth analysis of a PDF attack, down to the level of the code itself.
The complete 2010 “Top Cyber Security Risks Report” is available at http://dvlabs.tippingpoint.com/toprisks2010














