A recently patched vulnerability in the Slack desktop application for Windows can be exploited by malicious actors to steal and manipulate a targeted user’s downloaded files.
David Wells, a researcher at Tenable, discovered that version 3.3.7 of the Slack desktop app is affected by a download hijacking vulnerability that can be exploited by getting the targeted user to click on a specially crafted link pasted into a Slack channel. The security hole was patched by Slack with the release of version 3.4.0.
Wells found that slack:// links can be used to change the location where a user’s files are downloaded using the PrefSSBFileDownloadPath setting. An attacker could create a link that, when clicked, changes the targeted user’s download destination to a path specified by the attacker, including a remote SMB share.
The link, which can be set up to look as if it points to a trusted website, would look something like this:
slack://settings/?update={‘PrefSSBFileDownloadPath’:’<newDownloadLocation>’}
After the victim clicks the link, all the files they download in the future will go to the location specified by the attacker. Furthermore, Wells found that an attacker could manipulate the downloaded file stored in the location they control and it would be opened from there when accessed by the user.
For instance, an attacker can modify financial documents downloaded by the victim, or inject malware into downloaded Office files.
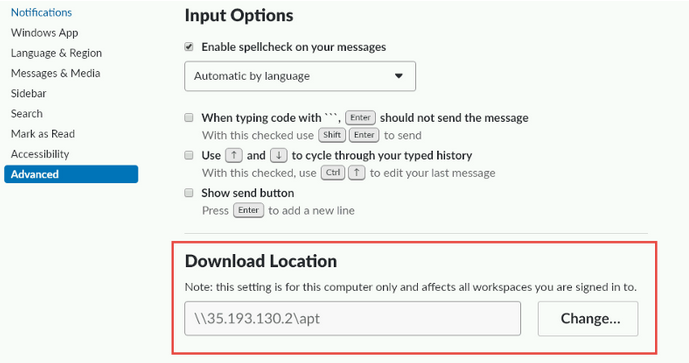
The specially crafted links that change the download location can be pasted to a Slack channel or a private conversation to which the attacker has access. This means that the vulnerability would mostly be useful to malicious insiders or attackers who already have access to the targeted organization’s Slack workspace.
However, Wells also discovered that an unauthenticated attacker can change the location of downloaded files using RSS feeds, which can be used to fetch data from third-party websites to Slack channels.
If the hacker can get the targeted user to click on a specially crafted RSS feed link posted anywhere on the web, the download location can be changed even if the attacker does not have access to the victim’s Slack workspace.
“This attack could be launched by someone outside of the organization but there are variables that might reduce the chances of success, like knowing which .rss feeds the target Slack subscribes to,” Tenable explained.
Since exploitation of the vulnerability requires user interaction and, in some cases, authentication, it has been classified as “medium severity.” Slack paid out a $500 bounty to the researcher who discovered the flaw.
The issue was reported to Slack via HackerOne on February 15 and it was patched with the release of version 3.4.0 on April 22. Some Slack installations are automatically updated, but users concerned that this vulnerability may be exploited against them should ensure that they are running the latest version.
Related: Slack Lists Cybersecurity Risks Ahead of Going Public
Related: Slack, GitHub Abused by New SLUB Backdoor in Targeted Attacks














