Many cybersecurity professionals working in the energy sector are concerned that an attack on their organization’s industrial control systems (ICS) could have “catastrophic” consequences, according to a study conducted recently by Dimensional Research on behalf of security and compliance solutions provider Tripwire.
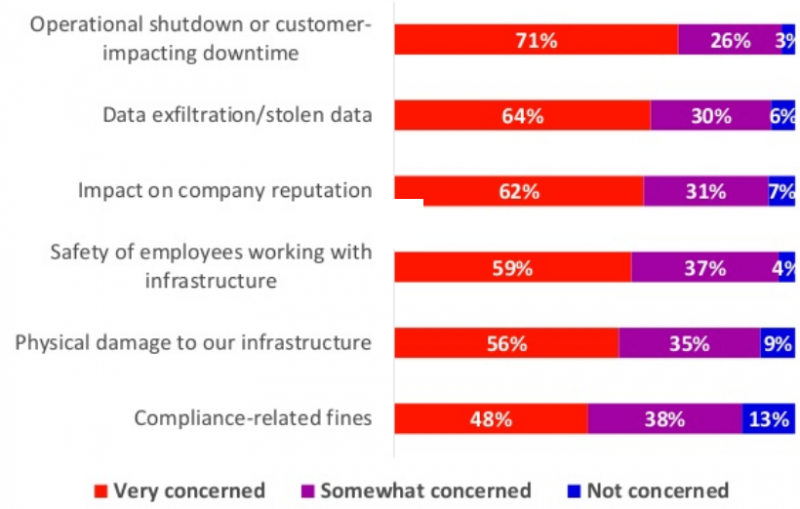
Of the more than 150 respondents, including IT and OT security professionals in energy and oil and gas companies, 91% say they are worried about the risk of attacks on ICS. Nearly all respondents are very concerned or somewhat concerned about an attack leading to operational shutdowns or downtime that impacts customers.
Other areas of major concern include physical damage to infrastructure, employee safety, impact on the organization’s reputation, and data theft.
Seventy percent of the cybersecurity professionals who took part in the survey say they are worried about an attack on ICS resulting in a “catastrophic event,” such as an explosion at the facility, and 90% are concerned that an attack could lead to equipment malfunction or failure.
Learn More at SecurityWeek’s ICS Cyber Security Conference
Nearly two-thirds of respondents believe their company’s investment in ICS security is sufficient, while 28% believe it’s insufficient. Of those who believe their current investment is not enough, 56% say their company would increase the budget if they are hit by a significant attack, and 53% believe management just needs additional information on the threat.
In fact, 59% admit that the recent incidents involving Trisis (Triton), Industroyer (CrashOverride), and Stuxnet malware have led to an increased budget. One-third say they haven’t received additional funding for cybersecurity, but they are aware of the threats.
“It’s encouraging to see that companies have increased their security investment somewhat,” said Tim Erlin, vice president of product management and strategy at Tripwire. “However, it’s concerning that more than half would wait for an attack to happen before investing properly, given what’s at stake with critical infrastructure. The energy industry should invest in establishing more robust cybersecurity strategies, with a proper foundation of critical security controls and layers of defense.”
High-profile pieces of malware such as Trisis and Industroyer have had a significant impact on security investments, but incidents involving ransomware have had the same degree of impact, the study shows.
While a majority of respondents have named lack of budget and investment (62%) the main barrier to meeting ICS security goals, others named the lack of talent and expertise (22%), and the complexity of the technology their are using (16%).
A report published recently by Kaspersky Lab showed that the energy sector was targeted by cyberattacks more than any other industry, and many of the vulnerabilities disclosed last year impacted products used in this sector.
Related: Non-Targeted Malware Hits 3,000 Industrial Sites a Year
Related: Increasing Number of Industrial Systems Accessible From Web
Related: One-Third of Industrial Networks Connected to Internet












