A fairly new piece of ransomware has been found leveraging pen-testing/attack tools for a more targeted approach of getting installed on compromised systems, Microsoft researchers warn.
Dubbed Samas (Ransom:MSIL/Samas), this piece of malware surfaced in the last quarter when Microsoft’s researchers noticed that it requires additional tools and components during deployment. It all starts with a pen-testing/attack server that searches for potentially vulnerable networks to exploit, but the result is the same as with other ransomware: user’s files end up encrypted.
Microsoft Malware Protection Center (MMPC) researcher Marianne Mallen explains that a publicly-available tool called reGeorg is used for tunneling, and that the actors behind this ransomware also use Java-based vulnerabilities such as direct use of unsafe Java Native Interface (JNI) with outdated JBOSS server applications.
Additionally, the malware operators were observed using information-stealing malware such as Derusbi/Bladabindi to gather login credentials. All of the stolen credentials are listed in a text file, and used to deploy the malware and its components through a tool called PsExec (psexec.exe), which lets users execute programs on remote systems.
The deployment is performed through batch files detected by Microsoft as Trojan:BAT/Samas.B and Trojan:BAT/Samas.C, with the former also used to delete the shadow files through the vssadmin.exe tool. There is also a Trojan:MSIL/Samas.A malicious application involved.
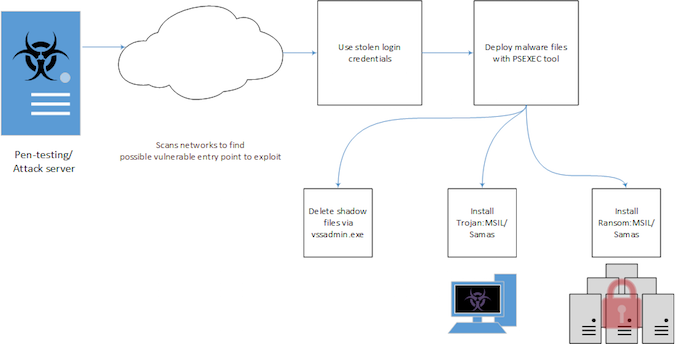
Samas was designed to search for specific file extensions that are related to backup files in the system and delete them. The Trojan also makes sure that these files are not locked up by other processes by simply terminating these processes, thus ensuring that it can perform its operation unhindered.
Once all of the initial operations were performed, Microsoft explained, the Samas ransomware starts encrypting files in the system using the AES algorithm. It also renames the encrypted files with extension encrypted.RSA and displays a ransom note to inform users what happened to their files, after which the ransomware also deletes itself from the system.
Interestingly, researchers noticed that, while the ransomware initially used WordPress as its decryption service site, it then moved to a more obscure Tor site in an attempt to remain anonymous.
While reputable anti-malware solutions should be able to detect this threat, users and system administrators can employ additional security measures to prevent infection. These include strong password policies, disabled Office macros, and always up-to-date software, which ensures that malicious programs cannot exploit already patched vulnerabilities.
Ransomware has emerged as one of the biggest threats as of late, fueled by the proliferation of ransom-as-a-service (RaaS) and because it can provide cybercriminals with potentially high gains with minimal effort.















