An analysis of the reservation systems used by more than 1,500 hotels around the world revealed that over two-thirds expose user information and allow someone to cancel bookings.
Candid Wueest, principal threat researcher at Symantec, has analyzed the websites used by 1,500 hotels located across 54 countries, including two-star hotels in the countryside and five-star resorts. It’s worth noting that one website may serve tens and even hundreds of individual hotels.
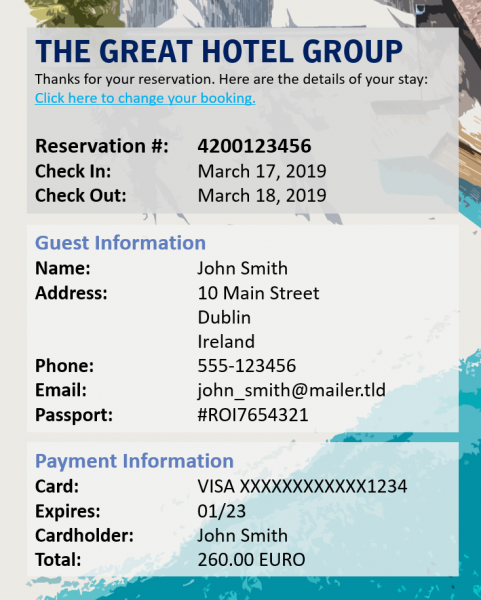
The problem is related to the confirmation emails sent by some hotels to customers when a reservation is made — 57% of the sites tested by Symantec sent these types of emails. The messages contain a link that takes the customer directly to their reservation on the hotel’s website, without them having to manually log in.
However, the URLs sent by 67% of the 1,500 hotels include the booking reference code and email address of the user — this data is used to authenticate the customer.
Each hotel’s website loads content from third-party companies, such as advertisers, analytics services, search engines, and social media networks. These services are provided the direct access URL, which enables them or malicious insiders to access users’ reservations, view their personal details, and even cancel their booking.
The exposed information can include full names, email addresses, postal addresses, phone numbers, the last four digits of payment cards and their expiration dates, and even passport numbers.
Wueest also found that 29% of hotel websites fail to encrypt the URLs sent via email to customers, which allows them to be intercepted if the user clicks the link while on a public internet connection, such as the ones in hotels and airports.
Researchers discovered recently that the reservation systems used by several major airlines expose data in a similar manner.
During his analysis, Wueest also noticed that the booking reference included in the links sent out by hotels can be obtained via brute force or enumeration attacks. In many cases, the code is incremented from one booking to the next, allowing an attacker who knows the targeted user’s email address or last name — depending on what type of information the URL includes — to easily obtain their booking reference number and access their reservation.
“Such an attack might not scale well, but it does work well when an attacker has a specific target in mind or when the target location is known, for example a conference hotel. With some websites, the customer’s email or name is not even needed on the backend—all that is required is a valid booking reference code,” Wueest explained.
According to the researcher, malicious actors could find the information exposed by these reservation systems highly useful. They could cancel someone’s reservation for fun or as a form of revenge, or they could attempt to damage a hotel’s reputation as part of a sabotage or extortion operation.
The exposed data could also be useful to scammers looking to make their messages more convincing, or advanced persistent threat (APT) actors, which have been known to target the hospitality sector, Wueest said.
The researcher has reached out to the hotels whose websites he analyzed, but a quarter did not respond at all within six weeks. The ones that did respond mainly promised to investigate the issues and take action to address them. Interestingly, some admitted that they were still in the process of becoming GDPR-compliant, while others were surprised to find out that the third-party service providers they had been using had not been GDPR compliant.













