The check-in links sent to customers by several major airlines from around the world can allow hackers to obtain passengers’ personal information and possibly make changes to their booking, mobile security firm Wandera warned on Wednesday.
Members of Wandera’s threat research team noticed in December that the links sent by Air France to customers through the company’s e-ticketing system are not protected by any type of encryption. These links are typically sent by companies via email or SMS and they are used to initiate the check-in process.
Further analysis revealed that similarly unprotected links were sent out by other major airlines as well, including Southwest in the US, KLM and Transavia in the Netherlands, Vueling and Air Europe in Spain, Jetstar in Australia, and Thomas Cook in the UK.
The problem is that the check-in links sent by these airlines to their customers initiate a connection over HTTP instead of HTTPS.
The link itself, as Wandera VP of Product Michael Covington told SecurityWeek, includes a record locator, the origin of the flight and its destination, and, in some cases, the passenger’s name. Airlines use this data to identify each passenger and provide access to details of their reservation.
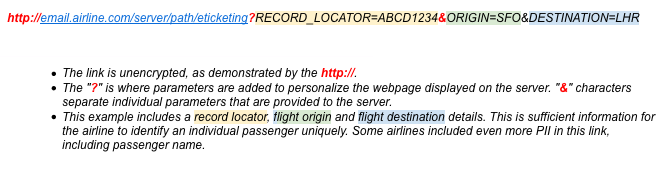
An attacker who can intercept a user’s traffic – for example, by compromising a public Wi-Fi connection – can leverage these credentials to gain access to the targeted user’s online check-in page.
Depending on the airline, the check-in service can provide access to data such as email address, name, gender, passport information, nationality, phone number, partial payment card information, booking reference, flight details (flight number, seating data), and even the complete boarding pass. In some cases, the attacker could also make changes to the data provided by the legitimate user.
“Boarding procedures vary from airport to airport and can be more or less secure. The most concerning aspect of this vulnerability is that in some cases a hacker or criminal can print a victim’s boarding pass and could even attempt to board a scheduled flight,” Wandera researchers explained.
The security firm pointed to a recent news report claiming that a man traveling from the UK to Poland boarded the wrong airplane and ended up in Malta. The incident raised concerns about boarding pass screening as the man had a ticket for Poland.
Wandera believes airlines should encrypt communications during the check-in process, they should implement additional authentication mechanisms for processes that involve access to personal information (especially if that information can be edited), and use one-time tokens for direct links delivered via email or SMS.
SecurityWeek has asked Wandera if it’s possible that a single e-ticketing platform is used by all the impacted airlines, but the security firm believes the weakness is not introduced by a single platform.
“Based on my assessment of the data and conversations I’ve had with the airlines, I’m fairly confident that this vulnerability impacts more than one platform,” Covington explained. “While a subset of the airlines may use a common platform, there are sufficient variations in how these systems communicate that I believe there to be several e-ticketing systems involved.”
“I suspect this boils down to an industry-wide decision to make online check-in easy; they’ve essentially prioritized usability over security. The entire problem goes away if they simply made the e-mail/SMS links one-time use,” he added.
Wandera notified each of the impacted airlines in December 2018 and January 2019, and said it had also shared its findings with government agencies in charge of airport security.
“Some have responded and indicated that they are investigating the issue,” Covington told SecurityWeek. “Unfortunately, we have not been able to verify that any fixes have been implemented. Our researchers have confirmed that some of the e-ticketing systems are still exposing data, so the problem has not been resolved.”
Other researchers revealed recently that a vulnerability affecting a reservation system provided by Spain-based Amadeus, which is used by hundreds of airlines worldwide, could have exposed the details of millions of passengers.
Related:Travel Booking Systems Expose User Data













