Data from vulnerability assessments conducted by security consulting firm IOActive in the past years shows some improvements in vehicle cybersecurity.
Since 2013, IOActive has spent thousands of hours every year analyzing vehicle cybersecurity, and the company has published several research papers on this topic. A report made available in 2016 showed that half of the flaws found at the time had an impact level of critical (25%) or high (25%).
The company describes critical vulnerabilities as issues that have an “extreme impact” on a vehicle if exploited, they would likely receive media attention, and are almost certain to be exploited. High severity flaws have a “major impact,” they could represent a regulatory violation, and they are relatively easy to find and exploit even by a less skilled attacker.
IOActive on Tuesday published a follow-up report to the one from 2016. The latest data, collected in 2016 and 2017, shows that only 10% of the vulnerabilities were critical and 23% were high in terms of impact.
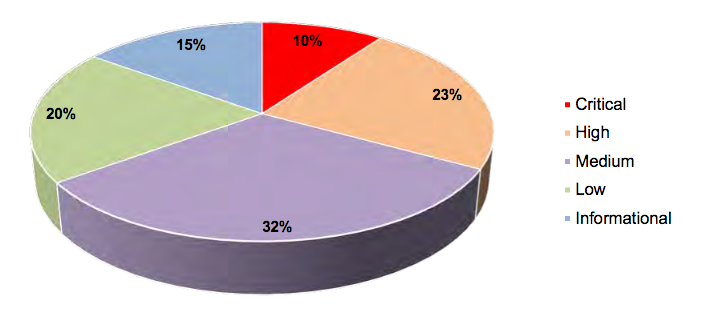
“Critical-impact vulnerabilities have decreased 15 percentage points, while the distribution of medium-and low-impact vulnerabilities has increased. This is likely the result of better security awareness and user separation. We’ve seen significant growth in the design of vehicle systems to incorporate security from the start. This includes making sure that the processes that handle data are running with limited privileges, which helps lower the impact of the most likely attacks,” IOActive said in its latest report.
In terms of likelihood of exploitation, the percentage of critical flaws has increased from 7% to 11%, and the percentage of high severity flaws has decreased from 21% to 17%. However, a majority of the detected security holes fall in the medium or low likelihood categories, which means they are not easy to exploit or they require another vulnerability for exploitation.
“We’ve seen security architecture improve significantly but we’ve also seen an expansion in the number and scope of remote services that could be leveraged to attack the system,” IOActive said.
There have also been significant improvements in terms of overall risk posed by vulnerabilities. Six percent of the flaws discovered in 2016 and 2017 were assigned a critical risk rating and 22% a high risk rating. In comparison, the previous report classified 22% of flaws as critical and 18% as high risk.
As for attack vectors, which IOActive says are useful for determining how an attacker could target a system, the latest report shows that the most common vectors for the vulnerabilities discovered by the company are local access and network access. There has also been a significant increase in flaws that can be exploited over a serial connection, which requires physical access to the device.
“The large increase in local and serial attacks can be attributed to a shift in testing approaches. As security has become a more prevalent concern, more companies are providing documentation and debugging access to help identify vulnerabilities inside their systems. The automotive industry is also taking more of an interest in lower-level security features, like secure boot, which is reflected in the areas we end up testing,” researchers said.
The most common types of vulnerabilities identified in the latest report are coding logic errors (26%), memory corruptions (16%), privilege issues (14%), and information disclosure bugs (12%).
IOActive’s analysis shows that a majority of flaws, 59% require low-effort fixes and only 12% are difficult to patch.
Related: Misconfigured CalAmp Server Enabled Vehicle Takeover
Related: Security Vulnerabilities: A Threat to Automotive Innovation













