Cars are plagued by many serious vulnerabilities that malicious actors can exploit to gain access to a vehicle’s systems, according to a new study conducted by IOActive.
Over the past three years, the security firm’s Vehicle Cybersecurity Division has spent 16,000 hours analyzing connected cars. Using information obtained from publicly available research and its own private vehicle security assessments, the company has compiled a report that it believes can be highly useful for cybersecurity strategy and planning.
Researchers have demonstrated on several occasions in the past years that cars can be hacked both through local and remote attacks. The most recent demonstration was made by Charlie Miller and Chris Valasek, who showed that an attacker with physical access to a vehicle’s computer systems can bypass Controller Area Network (CAN) protections and hijack several functions, including steering, acceleration and brakes.
Of the vulnerabilities analyzed by IOActive, 25 percent have been rated critical and 25 percent as having high impact. Based on likelihood of exploitation, 7 percent of flaws are considered critical (i.e. publicly disclosed and are almost certain to be exploited), while 21 percent have been classified as high impact issues (i.e. relatively easy to detect and exploit even by an attacker with little skill).
Based on these factors, researchers determined that 22 percent of vulnerabilities can be assigned an overall risk level of “critical” and 18 percent can be placed in the “high” range.
There are several attack vectors when targeting a vehicle and, according to IOActive, the most common is the network (39%), followed by local (17%), cellular network (16%), CAN bus (10%), USB (13%) and serial (5%).
While network-based attacks, which include Ethernet and Web traffic, are the most dangerous, local attack vectors should not be neglected either. Experts pointed out that the availability of apps and third-party software modules can make local attacks just as significant.
The most common types of vulnerabilities found by researchers are information disclosure issues, coding logic errors, buffer overflows, hardcoded credentials, backdoors, and vulnerable dependencies (e.g. use of outdated libraries).
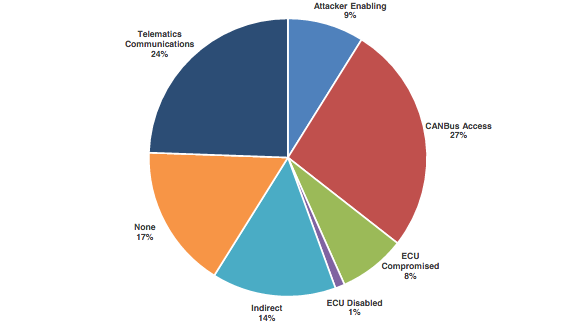
Experts determined that 17 percent of the issues they identified had no impact on the vehicle. However, the rest of the flaws can be exploited for CAN bus access, compromising telematics communications, escalation or attack chains, and compromising or disabling electronic control units (ECUs).
The good news is that a majority of critical vulnerabilities can be patched with relatively simple fixes. However, flaws related to design are more difficult or impossible to resolve once the system goes into production.
As for preventing security holes from making their way into modern vehicles, IOActive said half of the issues it found would not exist if industry best practices had been followed, particularly when it comes to authentication. Other prevention measures include code review and testing, secure coding practices, patch management and deployment procedures.
Related: FBI Reminds That Cars are Increasingly Vulnerable to Remote Exploits







