Researchers can earn up to $300,000 and a car if they manage to hack a Tesla Model 3 at this year’s Pwn2Own competition, Trend Micro’s Zero Day Initiative (ZDI) announced on Monday.
Pwn2Own 2019, scheduled to take place on March 20-22 alongside the CanSecWest conference in Vancouver, Canada, introduces an automotive category for which a Tesla Model 3 will be brought on site.
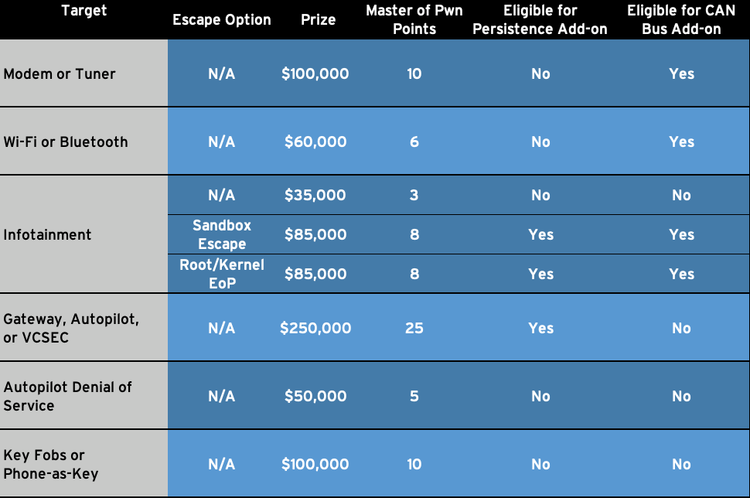
White hat hackers can earn between $50,000 and $250,000 for demonstrating an exploit against a Tesla’s modem or tuner, Wi-Fi or Bluetooth components, infotainment system, gateway, autopilot, security system, and key fob (including the phone used as a key). Some of the targeted components are also eligible for a bonus of $50,000 or $100,000 for persistence and a CAN bus hack, respectively.
“Along with the prize money, the first-round winner in this category will win a Tesla Model 3 mid-range rear-wheel drive vehicle,” ZDI said.
In the virtualization category, Pwn2Own participants can target Oracle VirtualBox, VMware Workstation and ESXi, and Microsoft Hyper-V Client. The highest prize is for Hyper-V – up to $250,000 and a $30,000 bonus for a privilege escalation on the host.
In the web browsers category, hackers can earn tens and even hundreds of thousands of dollars for sandbox escapes, Windows kernel privilege escalations, and VM escapes. The targets are Chrome, Edge, Safari and Firefox.
The enterprise category includes Adobe Reader, Microsoft Office 365, and Microsoft Outlook. Finally, the server-side category’s only target is Windows RDP, for which hackers can earn $150,000.
“Most of our server side targets moved to our Targeted Incentive Program, so they no longer need to be included in Pwn2Own,” ZDI explained.
The prize pool for this year’s event exceeds $1 million, and that does not include the money offered for hacking a Tesla.
At last year’s Pwn2Own, participants only took home less than $300,000 of the $2 million prize pool.
Related: IoT Category Added to Pwn2Own Hacking Contest
Related: Samsung Galaxy S9, iPhone X Hacked at Pwn2Own Tokyo












