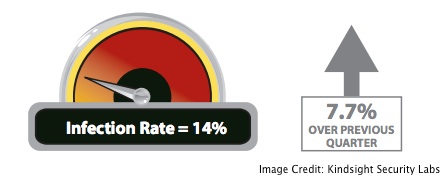
Approximately 14 percent of home networks were infected with malware from April through June 2012, according to a recent report from Kindsight Security Labs, a majority-owned subsidiary of Alcatel-Lucent.
Email messages luring users to websites running exploit kits remained the main method of infection during the second quarter of 2012, researchers wrote in the Kindsight Security Labs Malware Report for Q2 2012, released Thursday. The quarterly report identifies statistics and trends for malware infections in home networks, mobile devices, and computers connected through mobile adapters.
 Nearly 9 percent of residential households were infected by high-threat malware, such as a botnet, rootkit, or a banking Trojan. About 6 percent were infected with moderate-threat malware such as spyware, browser hijackers, and adware. Some households had multiple infections, Kindsight found.
Nearly 9 percent of residential households were infected by high-threat malware, such as a botnet, rootkit, or a banking Trojan. About 6 percent were infected with moderate-threat malware such as spyware, browser hijackers, and adware. Some households had multiple infections, Kindsight found.
“We saw an increase in the number of home networks infected as compared to first quarter 2012,” researchers wrote.
While not as publicly well-known as the Flame espionage malware, researchers were more concerned about the ZeroAccess botnet, whch grew to over 1.2 million nodes over the second quarter.
“In recent months, we’ve seen the ZeroAccess botnet update its command and control protocol and grow to infect more computers while connecting to over one million computers globally,” Kevin McNamee, security architect and director of Kindsight Security Labs, said in a statement.
ZeroAccess is a peer-to-peer botnet that focuses on ad click fraud and malicious bandwidth usage. Infected machines receive instructions from a command-and-control server directing them to click on ads on specific websites. The website owner collects per-click fees from the advertiser after generating fraudulent clicks using the botnet.
“The concern with ZeroAccess is that it is using the subscriber’s bandwidth maliciously which will cost them money as they exceed bandwidth caps. And, once the computer is compromised, it can also spread additional malware or launch new attacks,” McNAmee said.
ZeroAccess consumed bandwidth equivalent to downloading 45 full-length movies per month per subscriber during the second quarter.
Flashback, the Trojan that exploited a Java vulnerability to infect thousands of Mac OS X systems worldwide last spring, infected 10 percent of homes that owned at least one Mac, during the month of April, according to the report.
Speaking of malware that grabbed security headlines over the course of the quarter, Kindsight determined that 10 percent of computers infected with the DNSChanger Trojan still had not been cleaned by the end of June.
On the mobile side, approximately one out of every 140 devices on mobile networks was infected, Kindsight found. These devices were mainly compromised laptops and Android phones connecting to mobile networks. Apple also had its share of mobile woes during the second quarter, thanks to the questionable “Find and Call” app, which harvested user contact lists and spammed the contacts.
According to Kindsight, Android malware samples also increased by 300 percent over the past three months.
“While the increases in malware in this report are a concern, it is the types of malware that is driving this growth that is the thing to watch as we move into Q3,” researchers wrote.
The full report from Kindsight Security Labs can be found here in PDF format.
















