Thousands of instances of a temperature control system are exposed to remote attacks from the internet due to users’ failure to change default passwords and implement other security measures.
Researchers from Safety Detective discovered recently that refrigeration systems made by Resource Data Management (RDM), a Scotland-based provider of control and monitoring solutions, can be easily hacked from the internet. The experts say the vulnerable systems are housed by organizations from all around the world, including healthcare providers and major supermarket chains such as Marks & Spencer, Ocado and Way-On.
A Shodan search reveals over 7,400 devices accessible directly from the web, including many in Russia, Malaysia, Brazil, the United Kingdom, Taiwan, Australia, Israel, Germany, the Netherlands, and Iceland.
According to the researchers, the exposed systems can be accessed over HTTP on port 9000 (in some cases over ports 8080, 8100 or 80), and they are only protected by a known default username and password combination. The web interface can in many cases be accessed without authentication, but the password is needed when making changes to the settings.
Some of the systems can be easily identified via a simple Google search. Using Google and Shodan, researchers identified several types of impacted organizations, including a cold storage facility in Germany, a hospital and supermarkets in the UK, a pharmaceutical company in Malaysia, a food storage facility in Iceland, and an Italian food company.
Learn More About Control System Exposure at SecurityWeek’s ICS Cyber Security Conference
If an unauthorized user gains access to one of these systems, they can, among other things, change refrigerator, user and alarm settings. This can pose a serious risk in the case of supermarkets and cold storage facilities, where activating the defrost function could result in financial damage (i.e. spoiled products). The risk is even bigger in the case of hospitals, where refrigerators can store blood, organs and vaccines.
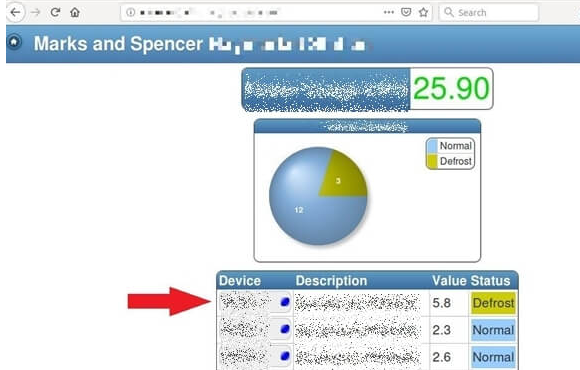
“The systems can be accessed through any browser. All you need is the right URL, which as our tests show, isn’t too difficult to find. We will not go into detail here, as it is not our intention to encourage the hacking of systems that could literally put lives at risk, but all it takes is a simple Google search,” explained Safety Detective’s Paul Kane.
Safety Detective contacted RDM, but the vendor initially did not take its findings seriously and asked the researchers to refrain from contacting them again. RDM later thanked Safety Detective, but blamed users and installers for the situation.
Contacted by SecurityWeek, RDM noted that only less than 50 of the 7,000 systems visible from the internet are on private networks and located behind a firewall. The company has urged customers and entities in charge of installing the temperature control system to ensure that the default password has been changed.
“To clarify the situation from RDM we would confirm that the default passwords must be changed by the installer at the time of setup. RDM does not have any control over where our systems go and who install them. We clearly state in our documentation that the default passwords MUST be changed when the system is installed. Its similar to an off the shelf router with default user names and passwords Admin Admin,” an RDM representative explained.
“We would also point out that we do not have remote connectivity to many systems and even though it is possible to upgrade our software remotely we are unable to do this without the consent of the owner. We will inform owners that we have new software available with new functions and features but ultimately it is up to them to request an upgrade which can be done via USB locally or by there installer / maintainer remotely,” they added.













