On Monday, shortly after Australian health insurer Medibank said it will not pay a ransom following a recent cyberattack, the BlogXX/REvil ransomware gang threatened to make stolen Medibank customer information public.
Medibank disclosed the cyber incident on October 12, saying that no ransomware was deployed on its systems, albeit admitting days later that customer data might have been exfiltrated.
The health insurer confirmed on Monday that the attackers compromised the personal information of roughly 9.7 million customers, including names, addresses, birth dates, and email addresses. For hundreds of thousands of customers, health-related data was also accessed.
Medibank said it believed that the attackers likely exfiltrated all the data they were able to access, but added that no ransom would be paid, as it would not guarantee the return of the stolen data or the fact that it would not be made public.
Shortly after the company’s announcement, however, the BlogXX ransomware gang wrote on its leaks website that it would publish the stolen data within 24 hours.
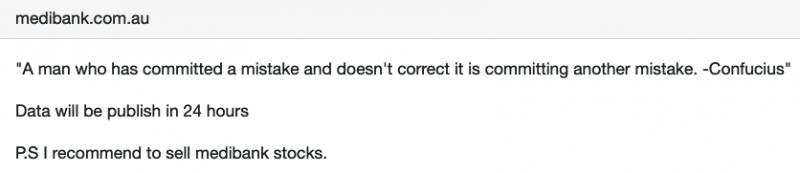
BlogXX emerged in April 2022, when the REvil ransomware gang’s leaks website started redirecting visitors to a new site, claiming to be a reborn operation. REvil made an exit in October 2021, after law enforcement reportedly seized its servers.
Based on multiple similarities with REvil, including the use of the Sodinokibi name (the initial name of REvil) and the reuse of REvil code, BlogXX is at least connected to REvil, if not a relaunch of the infamous ransomware operation.
In a Tuesday post, Medibank announced that it was aware of the ransomware gang’s claims, saying that it took into consideration the possible publication of the data and warning customers that the threat actor might attempt to contact them directly.
“We are working with the Australian Government, including the Australian Cyber Security Centre and the Australian Federal Police. The Australian Federal Police is investigating this cybercrime and trying to prevent the sharing and sale of our customers’ data,” the company said.
Medibank reiterated that it would not pay a ransom, saying that this “decision is consistent with the position of the Australian Government.”
Related: Medibank Confirms Data Breach Impacts 9.7 Million Customers
Related: New Malware Samples Indicate Return of REvil Ransomware
Related: Australia Flags New Corporate Penalties for Privacy Breaches















