SAN FRANCISCO – RSA CONFERENCE 2016 – Cloud security and compliance solutions provider Qualys has announced a new solution that gathers and correlates data from vulnerability scans and threat feeds to give organizations a view of their potential exposure to threats.
While the company has previously offered threat intelligence modules from partners for its cloud-based platform, Redwood City, Calif.-based Qualys now has a solution dedicated to helping customers prioritize their threat remediation efforts.
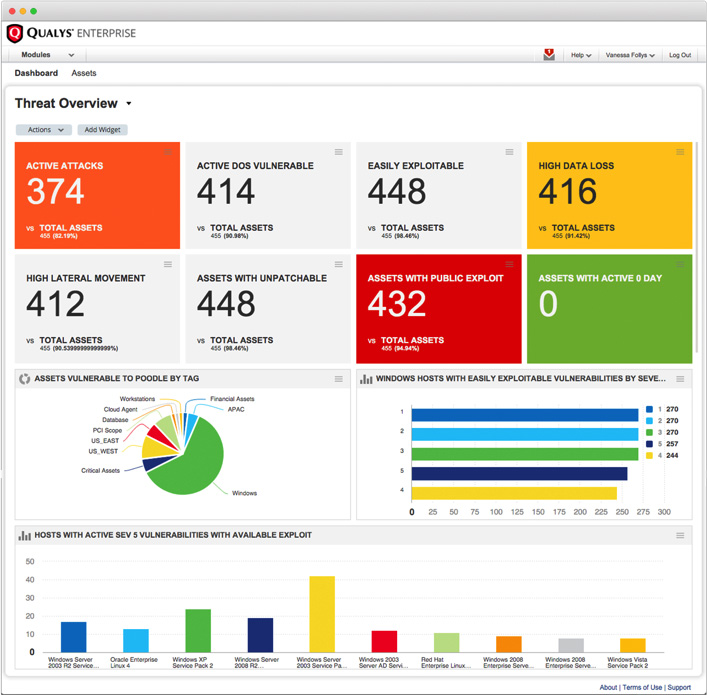
Built on the Qualys Cloud Platform, the new ThreatPROTECT offering lets customers visualize, prioritize and take action to minimize exposure from vulnerabilities related to the threats that matter most to their environments.
Leveraging vulnerability data collected via Qualys scanners and via Qualys Cloud Agents, ThreatPROTECT correlates the data with Real-time Threat Indicators (RTI) from multiple industry sources, providing customers with a dashboard that provides insight into which vulnerabilities they should fix first.
“RTIs are external data points that enrich and provide context when correlated with vulnerability scan data collected by Qualys,”the company explained. “RTIs can be used on a standalone basis or cascaded with each other to prioritize efforts for patching, or to select compensating controls to reduce exposure when patches are not available.”
Qualys gathers and correlates RTI information from its own research and from external sources, including Core Security, Exploit Database, Immunity, TrendMicro, VeriSign iDefense and others.