A team of researchers from Ruhr-Universität Bochum in Germany has analyzed 20 printers and multifunction printers (MFPs) from several vendors and discovered that each of them is affected by at least one vulnerability, including flaws that can be exploited to crash the device or obtain sensitive information that provides access to the organization’s network.
The experts conducted their tests on printers from HP, Brother, Lexmark, Dell, Samsung, Konica, OKI and Kyocera using a Python-based piece of software they named PRinter Exploitation Toolkit (PRET). The analysis revealed the existence of both old and new vulnerabilities and attack vectors that can be exploited locally or remotely.
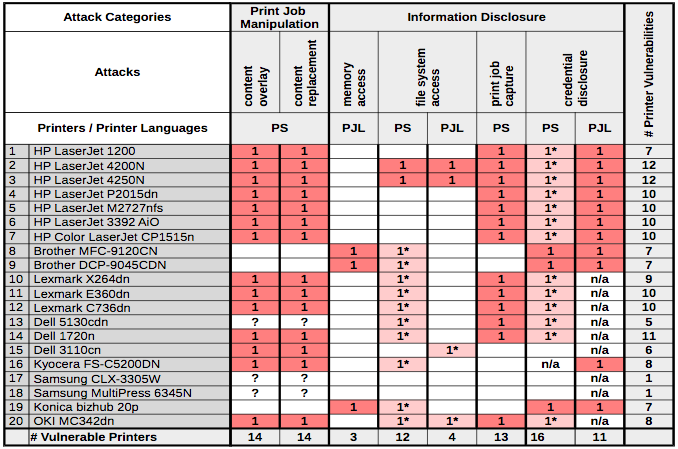
Some of the attack methods detailed by the researchers involve what they call PostScript malware. PostScript, created more than 30 years ago by Adobe, is a computer language used to describe the appearance of text and graphics on a page. The language is supported by all major printer manufacturers.
According to researchers, an attacker can abuse PostScript to manipulate documents, such as in the attack where thousands of printers were hijacked and made to print anti-Semitic flyers, or to capture the content of documents that are printed.
Such attacks can be launched through USB, remotely over the local network, or from the Internet via a malicious website using cross-site printing (XSP) and cross-origin resource sharing (CORS) spoofing.
Experts also showed how PostScript and Printer Job Language (PJL) can be leveraged to access the entire file system on some printers, including passwords for the embedded web server. This vulnerability has been known for several years, but experts say it still hasn’t been completely fixed.
“OKI MC342dn allows an attacker to execute one level of path traversal, where a directory called ‘hidden/’ is located which contains stored fax numbers, email contacts and local users’ PINs as well as the SNMP community string,” researchers said in their paper. “More interesting, however, is the fact that this MFP can be integrated into a network using features like Email-to-Print or Scan-to-FTP. An attacker could find passwords for LDAP, POP3, SMTP, outbound HTTP proxy, FTP, SMB, and Webdav as well as the IPsec pre-shared keys. This is a good example how an attacker can escalate her way into a company’s network, using the printer device as a starting point.”
They also discovered that buffer overflow vulnerabilities in the Line Printer Daemon (LPD) and the PJL interpreter can be exploited for denial-of-service (DoS) attacks and possibly even arbitrary code execution. PJL commands can also be used to cause physical damage to the device’s non-volatile memory (NVRAM) and gain access to sensitive information stored in the NVRAM, such as web server passwords.
These security holes can also be exploited locally, or remotely using XSP and CORS spoofing.
The experts have also analyzed Google Cloud Print, a service that allows users to print from anywhere, including their mobile device, to any printer. They showed that the Google service was also affected by some security issues, for which they earned a $3,133.7 reward from the search giant.
The researchers have also notified other affected vendors of their findings. However, they pointed out that the old vulnerabilities they had identified affected the latest versions of the firmware. In some cases, the vulnerabilities have been known for more than a decade, which they believe suggests that printer manufacturers don’t take security seriously, or they lack the proper security analysis tools.
Related: Hackers Can Abuse HP Enterprise Printers for Storage
Related: HP Enhances Network Printer Security














