A recent report from TXOne Networks, a Taiwan-based cybersecurity firm focusing on operational technology (OT), looks at OT security incidents and their sources, as well as the preparedness of organizations against attacks.
The report is based on a combination of data from a survey of over 400 CIOs conducted in September 2023 by Frost & Sullivan, and data collected by TXOne itself from more than 500 incidents that occurred last year in North America, Europe and the APAC region. The survey respondents represented organizations in the United States, Germany, Japan and the United Arab Emirates (UAE), with roughly 100 respondents from each country.
The survey found that 46% of organizations had dealt with an OT security incident in the previous 12 months. Of these incidents, 47% involved ransomware — the percentage was higher in the US and UAE, exceeding 50%, and the lowest was in Germany.
TXOne last year tracked 317 ransomware attacks in North America and 124 in Europe against companies that have OT systems. The government facilities, manufacturing and healthcare sectors were the most targeted. While these attacks were mainly aimed at IT systems, OT environments were also affected in 97% of cases.
The top three types of OT security incidents reported by respondents also included exploitation of vulnerabilities and malware infiltration.
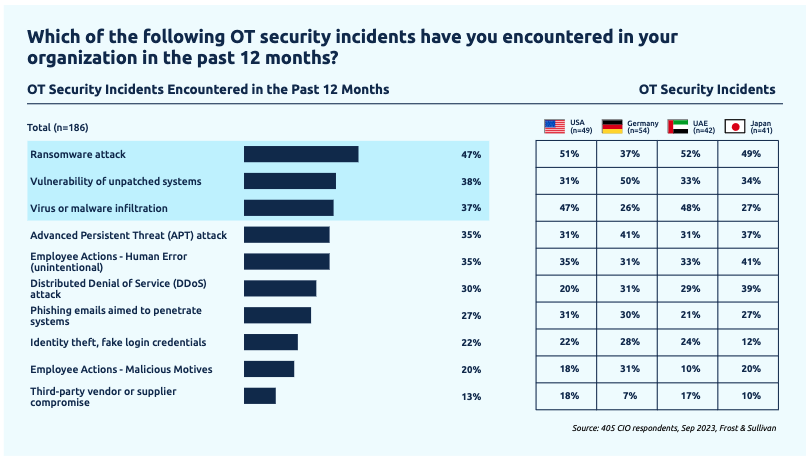
In the case of vulnerability exploitation, TXOne told SecurityWeek that organizations with OT systems are often aware of flaws being exploited in their environments, but they are unable to address the problem.
“Some legacy systems are no longer in their warranty periods; however, for technical or business concerns, those assets cannot be updated with the latest operating systems. For example, the existing apps on those assets often will not have any compatible versions with the latest, safer operating systems,” the cybersecurity firm explained.
While industrial organizations are often targeted in ransomware attacks, the survey showed that 76% are very or extremely concerned by attacks launched by state-sponsored threat actors. One perfect example are the recent US water sector hacks attributed to threat actors affiliated with the Iranian government.
When asked about the source of OT security incidents, the survey respondents most often named OT maintenance (52%).
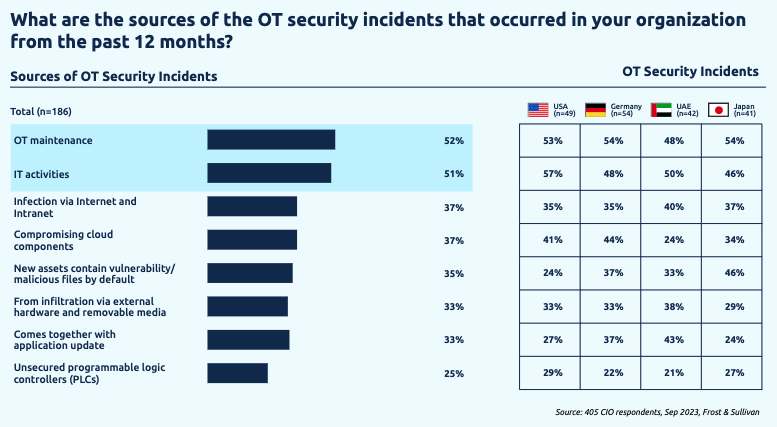
OT maintenance, TXOne clarified, includes updating software or firmware on assets, installing new applications, and reconfiguring settings. These activities can be done in-house by engineers or through third-party maintenance.
“A typical situation is when an asset goes into maintenance and it’s disconnected from other services, maintenance staff would install/copy something from that asset. That’s the point that the malware can enter the system, mostly through removable storage media,” the cybersecurity firm told SecurityWeek.
The report also looks into IT-OT convergence risks, cybersecurity complexity and maturity, OT/ICS cybersecurity management and investment, compliance, and regulations. The full report is available in PDF format on TXOne’s website.
Related: Ransomware Attacks on Industrial Orgs Increasingly Impact OT Systems: Survey
Related: Weapons Systems Provide Valuable Lessons for ICS/OT Security
















