OpenTitan is a project aimed at bringing the success of open source software to the silicon design space – specifically a silicon-level root of trust. The project achieved RTL Freeze in June 2023, and will be generating engineering sample silicon by the end of this year.
The project is managed by LowRISC, a UK non-profit organization founded in the Cambridge University computer lab in 2014 by Dr Gavin Ferris and Prof Rob Mullins (who also co-founded the Raspberry Pi Foundation with Pi’s creator Eben Upton in 2008).
LowRISC became steward of the OpenTitan project in March 2019, and has been working with partners including Google, Western Digital, Seagate and others.
Root of Trust
The root of trust (RoT) is the anchor upon which all subsequent operations are based. So, in simplistic terms, a device with no RoT separate from the operating system is very exposed. The OS must be accessible by applications and can therefore be accessed by attackers. If these attackers get beneath the application level (including security software) into the OS, then the device can be compromised invisibly. A separate root of trust is required that sits below the OS and below the BIOS and is inaccessible to attackers.
This separate root of trust can be used to verify that the boot process has not been modified and provide a secure home for cryptographic keys. Ideally, this RoT should be housed in a separate tamper-resistant chip. More specifically, such a silicon RoT (S-RoT) can help protect the device from bootkits, rootkits and firmware attacks.
“These are threats that execute before the OS is loaded,” explains Duncan Miller, endpoint security director at Tanium, “and can change the manner in which the OS verifies its integrity and ensures secure operation. Without a secure place to start from, and verification that hardware calls are in fact providing the data that they should during system initialization, later operations could be compromised in a way that is invisible to anything inside the operating system.”
OpenTitan can be described as a secure tamper-resistant cryptographically signed microcontroller. “It comes up independent of the operating system and provides certain security guarantees and services to the system – such as making sure the lowest levels of the operating system and drivers haven’t been compromised,” says Ferris. “Because if they have, whatever your antivirus says, it’s game over. It’s sort of academic because the damage has already been done.”
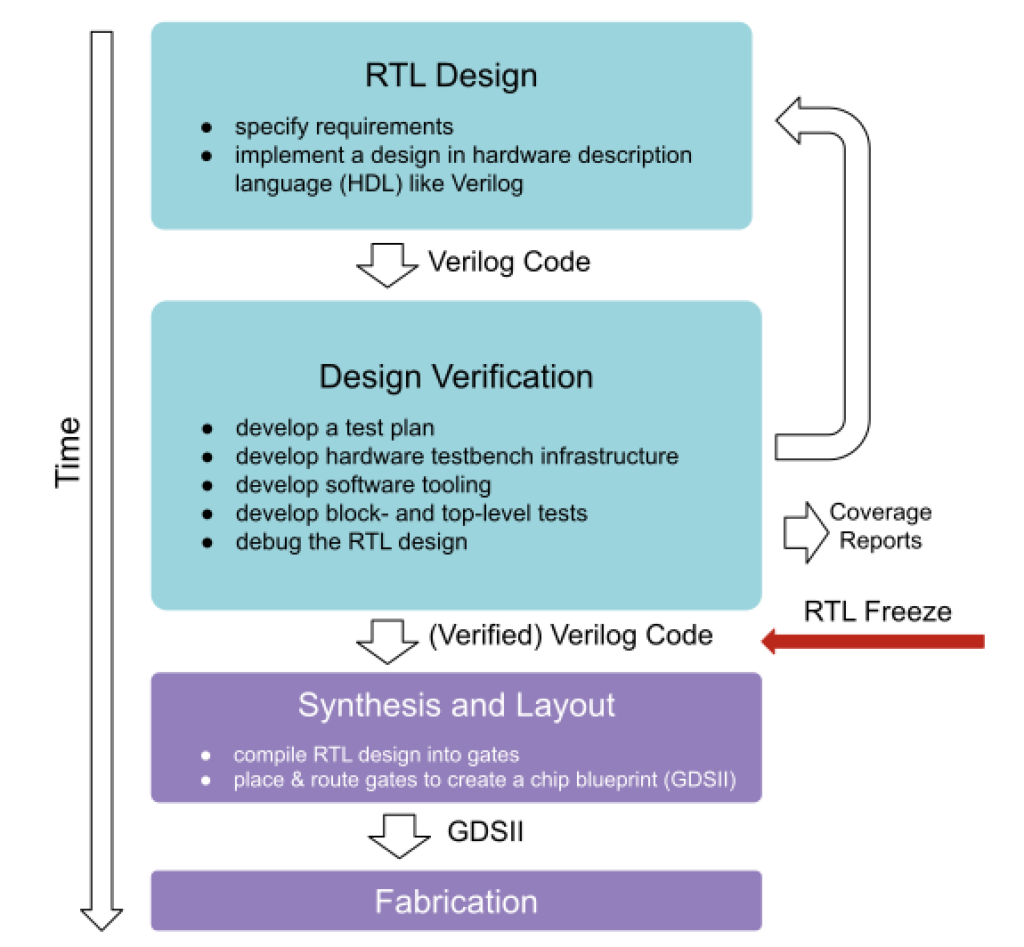
The OpenTitan S-RoT achieved its register-transfer level (RTL) freeze status in June 2023. This means the logical design is verified and fixed – a critical milestone in silicon development preceding fabrication.
Advantages of open source
The OpenTitan project is developing an open source S-RoT. It is far more complex than developing open source software. “But it’s worthwhile,” said Ferris. “The value of open source in terms of sharing foundational intellectual property and allowing companies to quickly build products is self-evident.”
There are two primary advantages in an open source S-RoT: transparency and availability. When chip level RoTs were first discussed and introduced (the first was Intel’s PTT in 2008) there was an undercurrent of concern that use of the device was now controlled by Intel. If the RoT verifies the boot firmware and authenticity of the operating system, then it can prevent anything not approved by the RoT designer from running.
“These devices are used to secure your food chain,” comments Ferris. “They’re used to store things like network access secrets independently of the operating system — which is good, but then who controls the thing you’re trusting?”
Over the years, the cybersecurity advantages of this ability have clearly won against the distrust inherent in lack of transparency into proprietary products. An open source S-RoT, however, delivers both security and transparency.
“OpenTitan has three core principles,” said Ferris: “flexibility, quality, and transparency. Transparency is fundamental. Developers build their own RoT operations for their products, and they anchor all the trust properties in the silicon below the operating system. To get widespread buy-in to OpenTitan, we need that level of transparency that you can only get with open source.”
While the S-Rot provides trust in the device operation, transparency provides trust in the S-RoT.
The second advantage of open source is availability. It would be fair to say that cyber defenders are facing a rapidly approaching perfect storm: the proliferation of very small, embedded devices (IoTs) with critical functionalities for OT and a dearth of defenses; the increasing sophistication and professionalism of malicious actors; and a regulatory focus on built-in security (NIS2 and the Cyber Resilience Act in Europe, and Biden’s ‘secure by design’ in the US).
The availability of an open source S-RoT will benefit all these areas.
OpenTitan and IoT/OT
Perhaps the most compelling use for OpenTitan is currently within IoTs, and ‘their more scary cousin, operational technology’. “This is where you put valves and actuators and sensors that are now on the network, when they weren’t before. That’s a huge and growing attack surface – the biggest ever security breach waiting to happen,” says Ferris.
“Device security – especially IoT security – requires knowing a device is what it says it is,” adds John Gallagher, VP of Viakoo Labs. “Many organizations have been deploying 802.1x certificates onto devices to establish this trust in a software-only manner. OpenTitan and other hardware approaches are gaining traction because they enable security to be baked into the device at the chipset level, rather than using software-based approaches later in the delivery chain.”
S-RoT is particularly suited to IoT devices, agrees Bart Stevens, senior director of product marketing at Rambus. “Many IoT devices still lack a Root of Trust. While programmable RoT solutions are built around a CPU, fixed-function silicon-based RoT solutions are typically compact enough and particularly well-suited for IoT embedded devices.”
First and foremost, adds Ferris, OpenTitan is a low power standalone chip. “It could fit into an IoT module without compromising the design. But just as importantly, by the end of this year, we will publicly release a reconfiguration. You can take your existing system on chip and put OpenTitan in a corner of it, so it’s sitting inside an existing design. It takes a little bit more silicon area, but it doesn’t require an extra chip on the board. That’s important when you’re looking at these low power consumption situations.”
Threats to a silicon root of trust
An S-RoT is designed to provide security to those parts of a device that can be attacked by a third party. The question remains, however: can the S-RoT itself be attacked? The answer is yes – any RoT is a target for attackers.
Stevens provides a summary of threats and solutions. “It should be made as secure as possible and include capabilities such as: siloed execution to ensure sensitive security functions can only be performed within a dedicated security domain; comprehensive anti-tamper and side-channel resistance to protect against multiple fault injection and side-channel attacks; layered security to provide multiple layers of defense and avoid a single point of failure; and multiple RoT instances to ensure isolation of resources, keys and security assets so each vendor, OEM or service provider can perform their own functions.”
Ensuring these functions and redundancies are part of the RoT solution, he adds, “ensures the device’s security and reduces the probability of any compromise.”
“All systems can be attacked,” agrees Ferris. “But we’ve taken five years developing OpenTitan, and have included all the knowledge and experience of our partners, including Google. The name itself is a nod to Google’s Titan range of RoTs that it has used to secure its servers, Chromebooks, and other devices.”
Since OpenTitan is open source, known threats and built-in countermeasures are publicly inspectable. He gives one side channel attack example. “Attackers can use lasers or electromagnetic pulses that cause the RoT to skip instructions.” This can cause the RoT to miss elements of its security checks, and allow the device to continue operating despite a loss of security in the protected device.
“So, we have a dual core processor that is in lockstep. It makes it very, very difficult for the attacker to interrupt the instructions at exactly the right point on both cores. Various hardening measures have been put in place to prevent this type of attack.”
He concedes that RoTs are a particular target for foreign three-letter agencies, with all their expertise. “But we’re open and always have been. Academics and researchers have probed our design for five years. Whenever a weakness has been found, it has been fixed before we reached the silicon stage. Being open enables lots of people to look, check, and notify us of any vulnerabilities, and for those to be addressed.”
In short…
What is the risk of a compromised device, asks Stevens. “In the most extreme cases, are there national security risks? If your device’s security is compromised, is there risk to human life, such as in self-driving cars or aerospace? Is there a financial risk, such as for chips meant for securing financial data on mobile phones or IoT devices? What is the risk to your company’s brand reputation if your chip is compromised?”
These security risks are rapidly being compounded by regulatory risk, as governments seek ways to ensure manufacturers provide products that are secure by design.
“A programmable hardware-based RoT,” he continued, “can protect against many security threats, including host processor compromise, non-volatile memory (NVM) key extraction, and corruption of NVM. It can also protect against test and debug interface attacks, side-channel and perturbation attacks, man-in-the-middle and replay attacks, and insider attacks.”
The S-RoT is rapidly evolving from a good thing to an essential part of computing in general, and IoT/OT in particular. OpenTitan, providing both transparency and availability (via GitHub), offers an attractive route for device manufacturers.
Related: DHS Working on Cloud-based Root-of-Trust to Secure Agency Email on Mobile Devices
Related: Intel Introduces Protection Against Physical Fault Injection Attacks
Related: Google Unveils KataOS ‘Verifiably-Secure’ Operating System for Embedded Devices
Related: Google Announces Open Source Silicon Root-of-Trust Project
















