A new ransomware family specifically targeting users of the Fortnite game is based on the open source Hidden-Cry malware, Cyren’s security researchers have discovered.
Fortnite is a highly popular game with a user base of over 250 million gamers worldwide, millions of which have recently attempted to qualify in the just-concluded Fortnite World Cup that had tens of millions of dollars in prizes.
Dubbed Syrk, the newly discovered ransomware is attempting to monetize on the popularity of the game by masquerading as a game hack tool for Fortnite. Once executed, the malware starts encrypting files on the victim’s machine, appending the .Syrk extension to them.
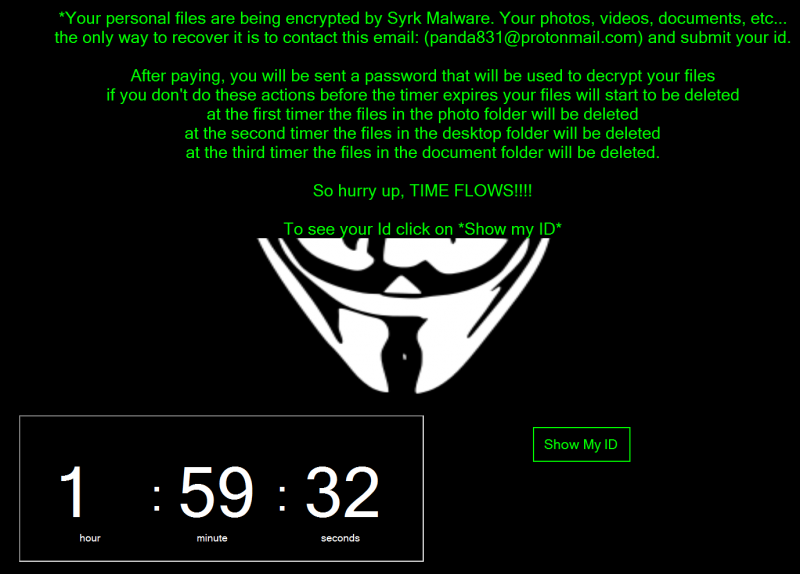
Analysis of the malware, Cyren explains, has revealed that the threat is, in fact, the open-source Hidden-Cry that adds a different extension to the encrypted files. The malware’s source code has been available on GitHub since the end of last year.
The ransomware attempts to trick users into paying the ransom as soon as possible by deleting files every two hours, but Cyren’s researchers believe victims can recover these files and that they can also decrypt the encrypted data without paying the attackers.
Syrk’s binary is 12MB in size, featuring a large number of files embedded in its resource section. These represent the main component for the malicious routine.
When executed, the ransomware also attempts to disable Windows Defender and User Account Control (UAC) through a registry tweak, and attempts to achieve persistence. It also monitors the system for tools that could terminate its process, such as Task Manager, Procmon64, and ProcessHacker.
The ransomware also attempts to infect USB drives attached to the system to propagate further.
The good news is that Cyren’s security researchers have discovered two methods for decrypting the encrypted data, because the files needed for that are present on the infected machines.
One of them is dh35s3h8d69s3b1k.exe, the Hidden-Cry decrypting tool, which is embedded as a resource in the main malware. Extracting and executing the file will result in the creation of a PowerShell script needed for decryption.
Additionally, the ransomware was observed dropping files that contain the ID and password necessary to decrypt the files. These are the -i+.txt, -pw+.txt, and +dp-.txt files in C:UsersDefaultAppDataLocalMicrosoft.
Syrk, the researchers reveal, also includes a clean-up mechanism, in the form of an executable that deletes the dropped files once a password was used to decrypt data.
Related: ‘Coordinated’ Ransomware Attack Hits 23 Towns in Texas















