An undercover operation by LegitScript, an online pharmacy verification service and anti-fraud company, has tied a single domain name registrar to roughly a third of all rogue pharmacy sites.
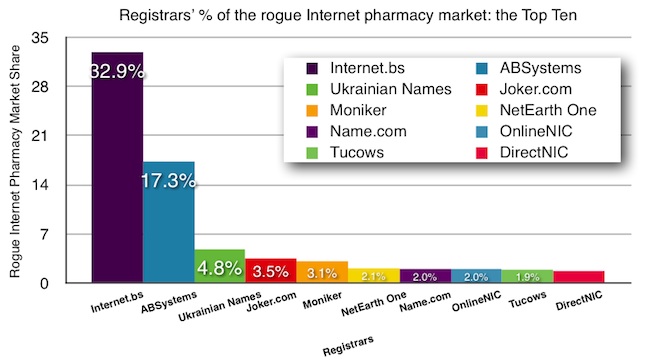
In a report, LegitScript names Bahamas-based registrar Internet.bs as the metaphorical man-behind-the-curtain for a chunk of the pharmacy sites in the company’s database. A second registrar, ABSystems, is believed to be responsible for more than 17 percent.
“Internet.bs currently identifies itself as having about 450,000 domain names –– that’s just about 0.2% of the total 225 million that Verisign recently estimated exist,” according to a statement by LegitScript. “But about one in three rogue online pharmacies in LegitScript’s database are registered with Internet.bs. If anything, our figures may be low: an analysis of the “not recommended” online pharmacies listed by the National Association of Boards of Pharmacy indicates that nearly 44% of those that are active and still online are with Internet.bs.”
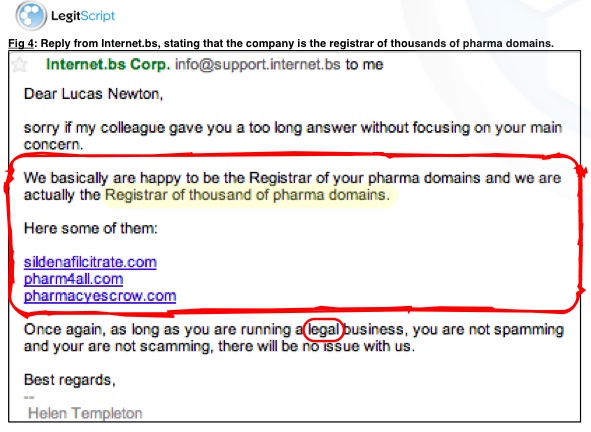
After reaching out to Internet.bs on more than “a dozen occasion spanning back to late 2010” to report hundreds of rogue pharmacies using its services, LegitScript decided to conduct an investigation into the registrar. Posing a cybercrime network called ‘Pay-Rx.biz’, LegitScript said it approached Internet.bs with a request to create thousands of websites selling controlled substances –all the while being clear that the drugs were counterfeit and that they had been shut down by regulatory authorities including the U.S. Food and Drug Administration (FDA) and Interpol.
“Despite being informed about the illicit nature of our business, Internet.bs was glad to help, emphasizing that it would ignore any notifications from drug safety authorities, and even suggesting ways for us to better protect our rogue online pharmacy network,” the company contended.
Not surprisingly, Internet.bs tells a different story, stating that it was tricked into registering 176 domain names by LegitScript as part of an effort by “ill spirited individuals” to tarnish the company’s reputation.
“By providing false or inaccurate Whois details they were also in breach of ICANN policies,” the registrar contended in a statement. “Furthermore fake registration details had also been used by the same malicious clan for many domain name extensions not covered by ICANN polices (.fr, .it, .uk, .us, .be, .eu, .pm, .re, .tv, .wf, .yt).”
“To those few dishonest persons out there who are trying to circumvent the laws and regulations by deliberately providing fake registration details or by blatantly acting against the laws of their country of incorporation or by ignoring rules and regulations of the respective registries and industry regulators, Internet.bs Corp. wants to stress that it will not provide a safe haven as it has just proudly demonstrated,” the company added.

In its report, LegitScript details a trail of emails in which the company – posing as Pay-Rx.biz – converses with Internet.bs about its business. According to the report, more than 71 percent of the rogue pharmacies on the Web are registered by just 10 registrars.
“Registrars, ISPs, search engines, registries, and the Internet community generally have vocally decried legislative or regulatory attempts to expand government control over the Internet, accurately noting that the Internet has thrived because it is autonomous and not operated or controlled by governments,” according to the report. “But this only underscores the importance of voluntary self-regulation, not merely by individual Registrars, but also by the Registrar community as a whole. Vacuums want to be filled: if ICANN and the Registrar community do not step up to firmly deal with cybercrime-friendly Registrars in their midst, it is inevitable that government authorities will seek to do so; if jurisdictional constraints make that difficult, governments will inexorably seek expanded authority and new tools. If the Internet community hopes to prevent that, it must insist that ICANN enforce its existing code of conduct against Registrars, like Internet.bs, who willingly serve as platforms for cybercrime.”