The number of internet-exposed industrial control systems (ICS) has continued to decrease over the past years, dropping below 100,000 as of June 2023, according to a report from cybersecurity ratings company Bitsight.
Companies and researchers regularly scan the internet for exposed ICS, and in the past decade they have reported seeing tens of thousands and even millions of systems, depending on their methodology and length of the study.
However, it’s interesting to see year-over-year trends from the same company, which presumably has a consistent methodology.
Bitsight has been tracking the number of internet-facing ICS, mapping these systems to its inventory of global organizations. It’s worth noting that while the company refers to the identified systems as ICS, they include — based on the targeted protocols — not only systems used in industrial environments, but also IoT, building management and automation devices, and other operational technology (OT).
The company’s analysis showed that the number of exposed systems has gradually decreased from roughly 140,000 in 2019 to less than 100,000 in June 2023.
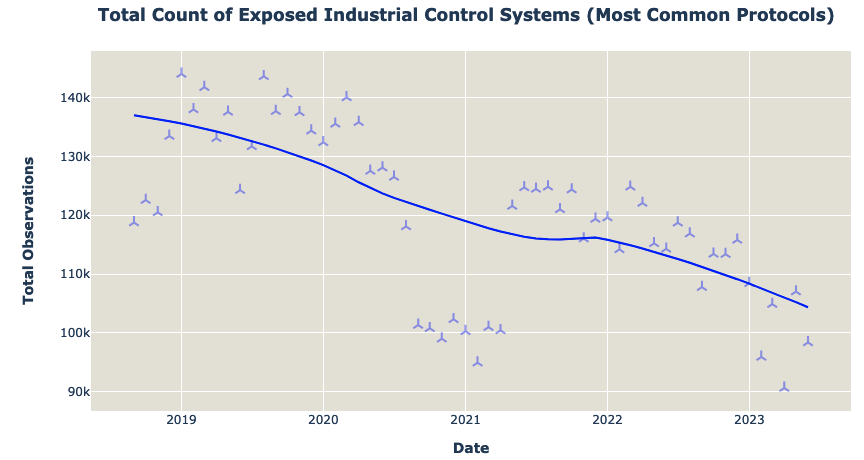
“This is a positive development, suggesting that organizations may be properly configuring, switching to other technologies, or removing previously exposed ICSs from the public internet,” Bitsight noted.
In addition, the number of exposed organizations has dropped from approximately 4,000 to 2,300 over the same period. Entities that still have public-facing systems include organizations across 96 countries, including Fortune 1000 companies.
The top 10 impacted countries are the United States, Canada, Italy, the UK, France, the Netherlands, Germany, Spain, Poland and Sweden.
The most impacted sectors are education, technology, government, business services, manufacturing, utilities, real estate, energy, tourism, and finance.
In 2023, the most commonly observed protocols were Modbus, KNX, BACnet, Niagara Fox, Siemens’ S7, Ethernet/IP, Lantronix, Automatic Tank Gauge (ATG), Moxa’s NPort, and Codesys.
In the case of the education sector, for instance, the most commonly seen protocols were BACnet, Niagara Fox and Lantronix, which are typically used for building automation and physical security systems.
“While the aggregate number of exposed ICSs has been trending downward, we detected unique behavior on a protocol-by-protocol basis,” Bitsight explained. “Exposed systems and devices communicating via the Modbus and S7 protocols are more common in June 2023 than before, with the former increasing in prevalence from 2020 and the latter more recently from mid-2022.”
“However, exposed industrial control systems communicating via Niagara Fox have been trending downward since roughly 2021. Organizations should be aware of these changes in prevalence to inform their OT/ICS security strategies. One of the first steps in mitigating OT risk is knowing where the risk is likely to lie,” the company added.
Bitsight also noted that companies should focus on securing specific protocols based on their location. For instance, systems using Codesys, KNX, Nport and S7 protocols are mainly in the European Union, while ATG and BACnet are primarily seen in the United States.
Learn More at SecurityWeek’s ICS Cyber Security Conference
The leading global conference series for Operations, Control Systems and OT/IT Security professionals to connect on SCADA, DCS PLC and field controller cybersecurity.
October 23-26, 2023 | Atlanta
www.icscybersecurityconference.com
Related: SANS Survey Shows Drop in 2023 ICS/OT Security Budgets
Related: NIST Publishes Final Version of 800-82r3 OT Security Guide
















