Clickjacking Scams Continue to Target Facebook Users. “Cheerleaders Gone Wild” Scam Lures Users to “Like” Without Knowledge
Yet another “clickjacking” scam is spreading on Facebook today, trying to lure users into checking out scantily clad cheerleaders “gone wild.”
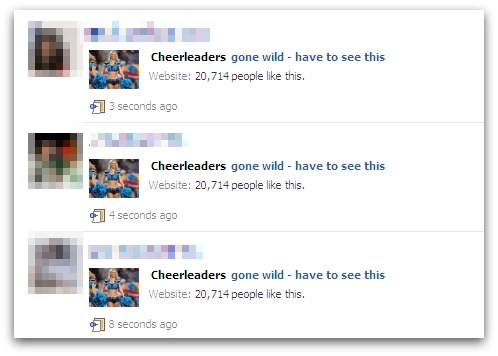
Clicking on a message link takes users to a page claiming they are about to access content “inappropriate for some users” as it “may contain shocking graphics, nudity or disrespect other individuals.” Designed to mirror an official Facebook warning, it requires the user to confirm they are 18 years old or older before proceeding. During the fake “verification” process, users are actually being tricked into confirming they “Like” the “Cheerleaders gone wild” page.
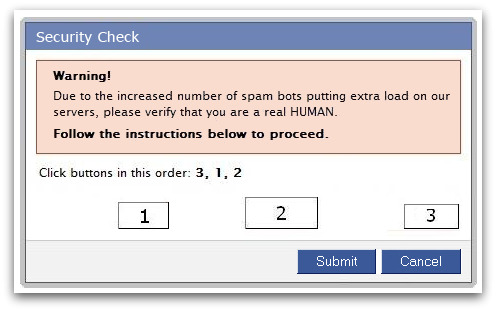
When users click on the verification buttons they are actually being clickjacked and are invisibly confirming to “Like” other pages including, “Funniest Videos On the Web” and “Free ringtones every day.”
Other recent scams include a fake “Dislike” button which claims to enable users to dislike items within facebook, as well as many “Survey” scams which often utilize clickjacking techniques.
Thanks again to Graham Cluely and the Sophos team for the tip!
















