“DroidLive” SMS Android Trojan Masquerading as a Google Library, Attempts to Utilize Device Administration API
A research team at NC State University led by Assistant Professor Xuxian Jiang and NetQin, have uncovered a new SMS Android Trojan that attempts to install itself as a device administration app, and capable of tapping into personal data and performing a mixture of nefarious activities on android mobile devices.
 Jiang, who is also Director of NetQin’s U.S. Security Research Center, explained that the android malware, dubbed DroidLive, attempts to disguise itself as a Google library, and receives commands from a Command and Control (C&C) server, allowing it to perform functions including sending text messages to premium numbers, initiating phone calls, collecting personal data, and more.
Jiang, who is also Director of NetQin’s U.S. Security Research Center, explained that the android malware, dubbed DroidLive, attempts to disguise itself as a Google library, and receives commands from a Command and Control (C&C) server, allowing it to perform functions including sending text messages to premium numbers, initiating phone calls, collecting personal data, and more.
Over the weekend, Jiang told SecurityWeek that this is new malware and not a variant of previously known samples, and appears to be the first to take advantage of the device administration API.
“Though this requires user consent, if such consent is given, DroidLive can obtain privileges closer to those granted only to the device’s firmware,” Jiang explained. “This Trojan attempts to hide itself by appearing as a Google library — all of its functionality is contained in a package that matches Google’s own package naming convention.”
How DroidLive Works
Jiang shared the following details on how DroidLive works, and provided the diagram below to help further explain how it uses Android’s standard inter-app communication layer:
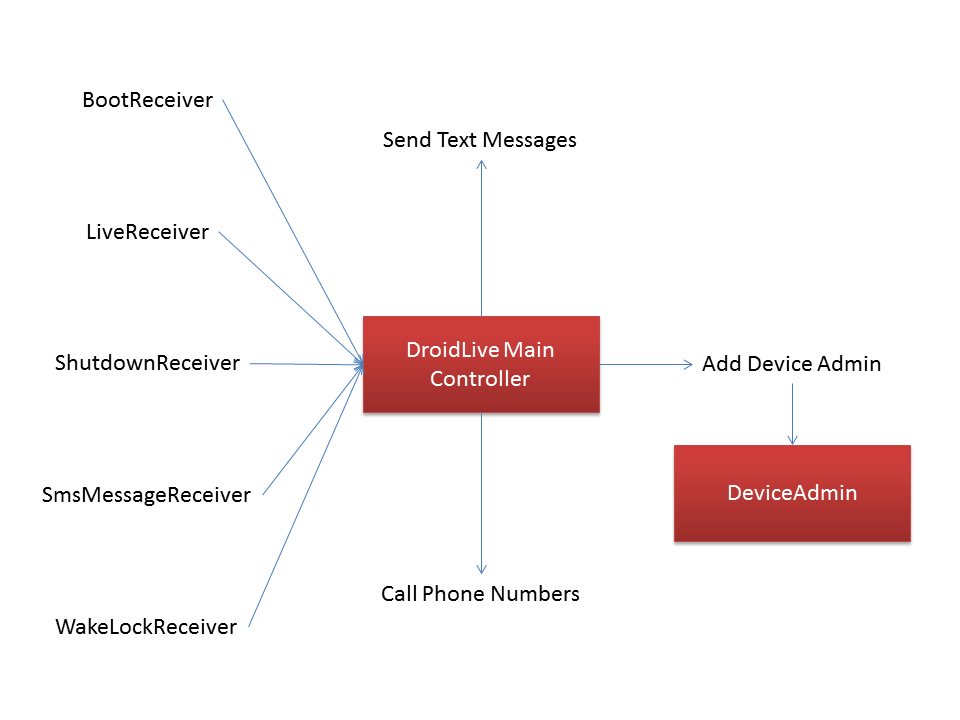
1. DroidLive’s heart is a main control service, MainService, which is invoked via the Android IPC mechanisms by other parts of the Trojan. This service takes action based on a string passed to it when it is invoked; these strings are in plain, human-readable text. MainService is initially invoked by other receivers that listen for a variety of (17) system events.
2. Once the malware has been initially invoked, it uses message queues and Android’s alarm functionality to periodically wake up and contact its C&C server. As part of this process, DroidLive sends a large amount of information to the server, including the device’s unique hardware identifier (IMEI), current cell tower identifier (CID), subscriber identifier (IMSI) and more. In return, the server sends a list of actions for the bot to perform.
3. DroidLive features several commands, which are handled by dedicated components. It can send text messages, make phone calls, or attempt to install itself as a device administration app. This last feature requires user consent, but if granted allows DroidLive privileges closer to those granted only to the device’s firmware. Inside the device admin code, it obtains a list of all the apps running on the device. Note this device admin-level access would allow other priviledged actions, such as wiping out all the data on the device.
Jiang told SecurityWeek that his team has discovered more than 10 distinct Android apps infected by the DroidLive malware, though none of those were found in the official Android Market. “Users can be infected by downloading and installing apps from various Android Markets,” Jiang said. “We find them from alternative marketplaces.”
While Jiang wasn’t able to provide any concrete number in terms of infected devices, he did warn that it could grow rapidly, similar to the case of DroidKungFu and AnserverBot. He also suggested that because DroidLive can be remotely controlled, it poses serious threats to Android users.
Android users should only download apps from reputable sources and always check reviews, ratings, and developer information before downloading.
At the time of publishing, the command and control server appears to still be operational. The server (IP addresses and domain intentionally omitted) appears to be a server located in China.












