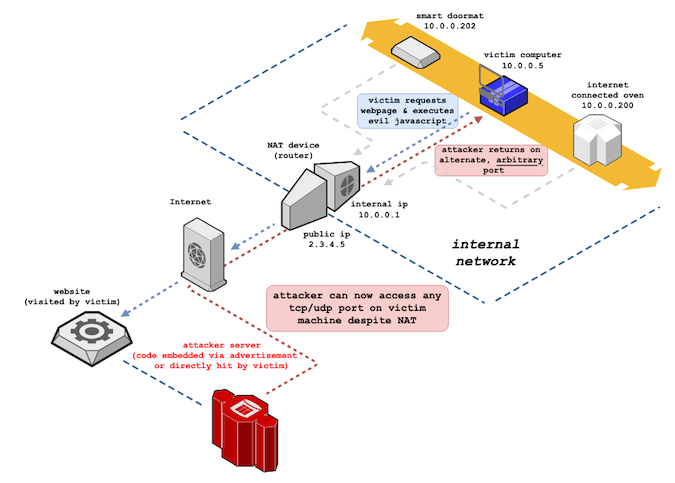
A newly identified attack method can bypass Network Address Translation (NAT) and firewalls, allowing the attacker to remotely access TCP/UDP services on the victim’s internal network, security researcher Samy Kamkar explains.
Dubbed NAT Slipstreaming, the attack can be triggered when the victim visits a specially crafted website, exploiting the browser and Application Level Gateway (ALG), a connection tracking mechanism present in firewalls, NATs, and routers.
According to the researcher, the attack chains “internal IP extraction via timing attack or WebRTC, automated remote MTU and IP fragmentation discovery, TCP packet size massaging, TURN authentication misuse, precise packet boundary control, and protocol confusion through browser abuse.”
Leveraging the fact that the destination port is opened by the NAT or firewall, the attack can bypass existing browser-based port restrictions. All major modern browsers are vulnerable to the attack, which is a new variant of the NAT Pinning technique that Samy Kamkar presented a decade ago.
The attack is based on the presence of ALG support in the NAT/firewall, a mandatory capability for multi-port protocols, such as FTP, IRC DCC, SIP and H323 (VoIP), and others.
NATs allow for multiple computers to connect to the Internet using a single public IP address, through creating a local network, where each system has a local IP address. When a computer attempts to connect to the Internet, the outgoing packets are rewritten to use the public IP address, which ensures that responses come back to the NAT.
The NAT also differentiates connections that internal hosts attempt to make to the same addresses/ports, by rewriting source ports. Through ALG, NATs can track multi-port protocols, making sure that the right data is delivered to the machine that requested it.
What the security researcher has discovered is that it is possible to “bypass victim NAT and connect directly back to any port on victim’s machine, exposing previously protected/hidden services.”
Such an attack, Kamkar says, starts with the victim visiting a malicious website or being served a malicious ad and continues with the victim’s internal IP address being extracted (via WebRTC over HTTPS or by performing a web-based TCP timing attack) and sent to the server.
Next, large TCP/UDP beacons are sent to overflow packet size and cause packet segmentation, and a “SIP packet” that contains the internal IP is generated, triggering APG connection tracking. The “SIP packet” ends up in its own TCP packet, without an accompanying HTTP header, and the TCP/UDP ports defined in packet are opened.
At this point, the ALG port forwards to the attacker-defined ports, as it is tricked into considering the port opened by the victim machine. The “attacker can now bypass victim NAT and connect directly back to any port on victim’s machine, exposing previously protected/hidden services,” the researcher notes.
“Once the client gets the packet sizes and internal IP address, it constructs a specially crafted web form that pads the POST data up until we believe the packet will become fragmented, at which point our SIP REGISTER containing internal IP address is appended. The form is submitted via Javascript with no consent from the victim,” Kamkar explains.
The attacker can check the rewritten packets on the server and automatically tell the client that the SIP packet was not as expected if the public IP address is not in it. Once the packet is in the expected boundary, the NAT is tricked that the SIP registration is legitimate and coming from a SIP client on the victim’s machine.
The SIP response from the server is hidden within an HTTP response to ensure it doesn’t trigger browser protections, deceiving the NAT into opening the port in the original packet sent by the victim, and tricking the router into forwarding the attacker-defined ports back to the internal victim.
“All from simply browsing to a website. Attack complete. Attacker can now connect to arbitrary TCP/UDP services running on victim,” the researcher concludes.
Related: ‘State of the Firewall’ Report: Automation Key to Preventing Costly Misconfigurations
Related: State-Sponsored Cyberspies Use Sophisticated Server Firewall Bypass Technique
Related: Hackers Using RDP Are Increasingly Using Network Tunneling to Bypass Protections














