Mozilla has already patched a Firefox vulnerability disclosed last week at the Pwn2Own 2017 competition by a team of researchers from Beijing-based enterprise security firm Chaitin Tech.
The Chaitin Security Research Lab team hacked Firefox with a SYSTEM-level escalation and earned $30,000. The experts used an integer overflow to break Firefox and an uninitialized buffer flaw in the Windows kernel to escalate privileges.
The integer overflow vulnerability, rated critical and tracked as CVE-2017-5428, was patched on Friday with the release of Firefox 52.0.1. No other security fixes or improvements are included in this release.
“An integer overflow in createImageBitmap() was reported through the Pwn2Own contest,” Mozilla wrote in its advisory. “The fix for this vulnerability disables the experimental extensions to the createImageBitmap API. This function runs in the content sandbox, requiring a second vulnerability to compromise a user’s computer.”
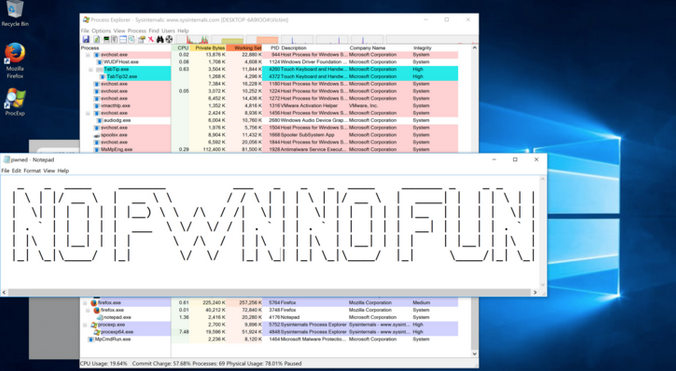
Chaitin Security Research Labs hacks Firefox and runs notepad.exe as SYSTEM
Moritz Jodeit of Blue Frost Security also targeted Firefox at the Pwn2Own competition, but he failed to demonstrate his exploit chain in the allocated timeframe.
In addition to Firefox, the Chaitin Security Research Lab targeted Safari, macOS and Ubuntu, and earned a total of $90,000 for its exploits.
The white hat hackers who took part in Pwn2Own 2017 received a total of $833,000 for finding 51 vulnerabilities in Windows, macOS, Ubuntu, Firefox, Edge, Safari, Flash Player, Adobe Reader and VMware Workstation.
No Chrome flaws have been disclosed at this year’s event and only one was reported at Pwn2Own 2016. It has become increasingly difficult to find critical security holes in Google’s web browser, which is why the company recently decided to increase rewards for remote code execution vulnerabilities to $31,337.
Related: Firefox 52 Warns of Login Fields on Insecure Pages
Related: Firefox 51 Patches Flaws, Introduces New HTTP Warning
Related: Mozilla Patches Firefox Zero-Day Exploited to Unmask Tor Users














