Mozilla released Firefox 51 this week and in addition to patches for several critical vulnerabilities, the latest version of the popular web browser introduces a new security feature designed to warn users when they access a login page that does not have a secure connection.
Firefox 51 addresses a total of 24 vulnerabilities, including five rated “critical” and six rated “high” severity.
The list of critical flaws includes a use-after-free bug in XSL (CVE-2017-5376), a bypass of ASLR and DEP protections (CVE-2017-5375), a memory corruption in the Skia graphics library (CVE-2017-5377), and various other memory corruptions that could lead to arbitrary code execution (CVE-2017-5374 and CVE-2017-5373).
The high severity vulnerabilities include information disclosure, privilege escalation and use-after-free weaknesses. One of the high impact flaws can be exploited by malicious extensions to install other extensions without the user’s knowledge.
Starting with Firefox 51, users will see a striked-out grey lock icon in the address bar when they access a website that collects passwords but doesn’t use HTTPS to secure the connection. In future releases, the web browser will display a similar icon and a warning message when the user clicks on a username or password field on a non-secure page.
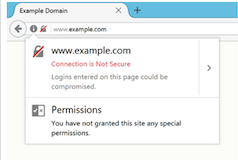
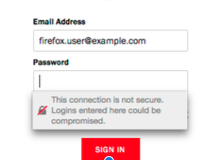
Mozilla has pointed out that implementing HTTPS is now easier than ever and an increasing number of websites have started using it. The organization says the percentage of login pages protected by HTTPS has increased from 40% to 70% since January 2016.
“To continue to promote the use of HTTPS and properly convey the risks to users, Firefox will eventually display the struck-through lock icon for all pages that don’t use HTTPS, to make clear that they are not secure,” Mozilla said in a blog post.
Mozilla recently patched a zero-day vulnerability leveraged to unmask Tor users. Some believe a law enforcement agency may have used the exploit as part of an operation targeting child pornography distributors.
Related Reading: Firefox to Display Error When Encountering SHA-1 Certificates
Related Reading: Mozilla Re-Enables Support for SHA-1 in Firefox
Related Reading: Firefox 50 Patches 27 Vulnerabilities













