More high-profile organizations are named as victims of the cyber-espionage campaign that involved an attack on Texas-based IT management and monitoring company SolarWinds.
Microsoft has confirmed that it has detected the malicious SolarWinds binaries delivered by the threat actor on its own systems as well. The tech giant took steps to remove the malware and claimed it had found no evidence that the attackers used its own systems to target others.
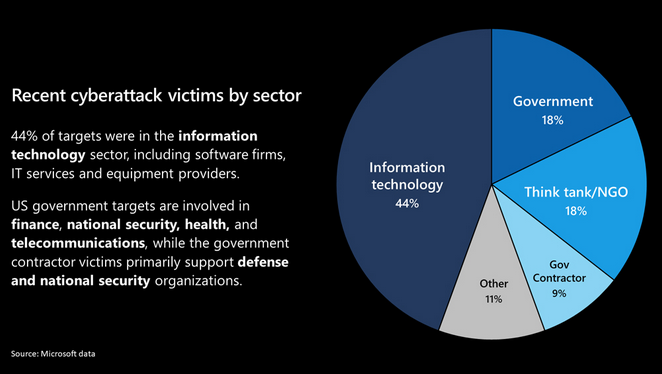
Microsoft said in a blog post on Thursday that it has identified more than 40 customers “that the attackers targeted more precisely and compromised through additional and sophisticated measures.” Roughly 80% of these targets are in the U.S., with some located in Canada, Mexico, the UK, Spain, Belgium, Israel and the UAE. The IT sector was the most targeted, followed by governments, NGOs and government contractors.
The attackers, described as a state-sponsored group possibly linked to Russia, compromised the build system for SolarWinds’ Orion products, allowing them to push trojanized updates to the company’s customers. SolarWinds says up to 18,000 customers may have received the malicious components.
While in many cases the hackers used the compromised SolarWinds system to deliver a piece of malware named SUNBURST, researchers noticed that a backdoor called Teardrop and a Cobalt Strike payload were also delivered to high-value targets. Microsoft’s description suggests that the 40 targeted customers are some of these high-value targets.
Politico reported on Thursday that the U.S. Energy Department and National Nuclear Security Administration (NNSA) were also targeted in the attack. Suspicious activity has been identified at the NNSA’s Office of Secure Transportation, at the DoE’s Richland Field Office, the Sandia and Los Alamos national laboratories, and the Federal Energy Regulatory Commission (FERC). However, DoE representatives said the attacks impacted business networks, but not “the mission essential national security functions of the department.”
Continuous Updates: Everything You Need to Know About the SolarWinds Attack
The Intercept reported that the attack also hit the city network of Austin, Texas.
Cybersecurity firm Palo Alto Networks said that it too detected an attempt to download Cobalt Strike to one of its SolarWinds servers, but the company claimed that its security systems blocked the attack. Palo Alto Networks noted that this attempt was detected before the SolarWinds hack came to light and the company is confident that the attackers did not breach its network.
According to container security firm Prevasio, the domain generation algorithm (DGA) used by the SUNBURST backdoor produces domain names that appear to include an encoded version of victim domain names. An analysis conducted by the company revealed roughly 100 potential victims, including many high-profile tech companies, but Prevasion has pointed out that the list it has published may not be entirely accurate as the domain names could have been generated by third-party tools and they may not actually belong to victims.
FireEye, one of the victims of the SolarWinds hack, and which was the first to disclose the attack, reported earlier this week that it identified and activated a killswitch for the SUNBURST malware.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned on Thursday that the SolarWinds supply chain attack was likely not the only initial access vector used by the attackers, but it has not shared additional information.
Related: Little-Known SolarWinds Gets Scrutiny Over Hack, Stock Sales
Related: FBI, CISA, ODNI Describe Response to SolarWinds Attack
Related: SolarWinds Removes Customer List From Site as It Releases Second Hotfix
Related: Group Behind SolarWinds Hack Bypassed MFA to Access Emails at US Think Tank













