Facebook parent Meta has officially unveiled a ten-phase kill chain model that it believes will be more inclusive and more effective than the existing range of kill chain models.
Cybersecurity theorists have long sought to understand the stages of an attack. The idea is simple: if you can recognize a stage in the attack process, you will be more able to disrupt the attack and protect your assets.
This has led to the development of kill chains – a sequential listing of the various stages. The original, and still iconic kill chain came out of Lockheed Martin in 2011: a seven-stage analysis of an attack known as the Intrusion Kill Chain. Lockheed Martin described the kill chain as “a systematic process to target and engage an adversary to create desired effects.” It is called a ‘chain’, because if you can weaken or degrade any one of the links, you can interrupt the attack process.
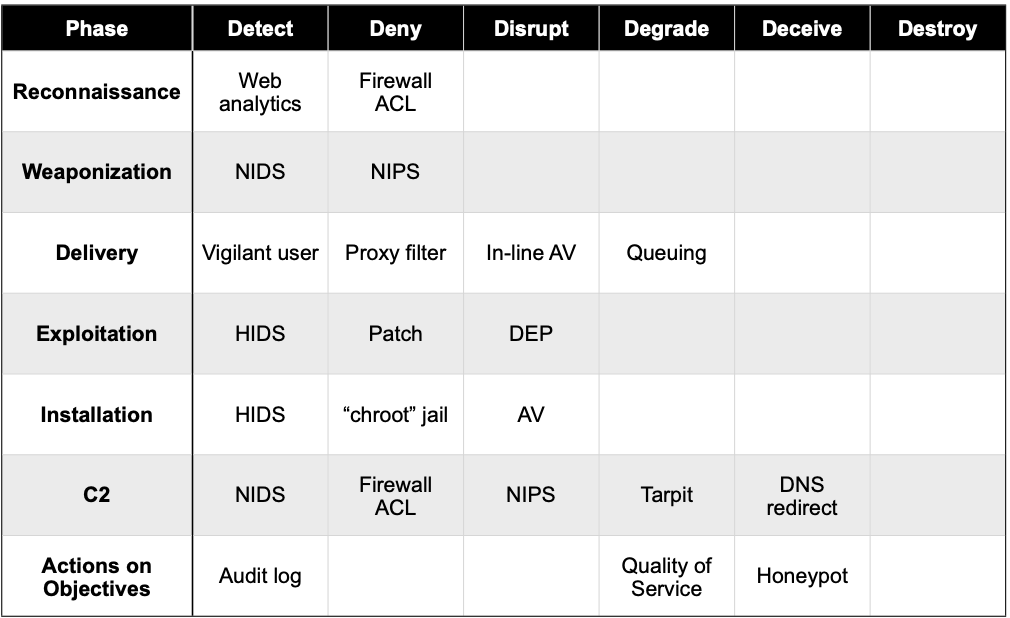

Over the years, there have been many attempts to define better or more efficient kill chains. But they tend to be ultimately unsatisfactory. The problem is the asynchronous relationship between attackers and kill chains: there are many different attackers using many different approaches to attack many different targets, that sometimes have many and often siloed response teams – while there is just one kill chain.
As a result, whichever kill chain is adopted by defenders, it tends not to be a full reflection of all attacks, all the time, everywhere. It is difficult for the right person to find the right link in the chain to disrupt.
This is the problem tackled by Meta’s Ben Nimmo and Eric Hutchins in a study titled Phase-based Tactical Analysis of Online Operations (PDF). Nimmo is Meta’s global threat intelligence lead. Hutchins is an investigator on Meta’s influence operations team. He was previously with Lockheed Martin and co-authored the white paper on the original Intrusion Kill Chain.
The Online Operations Kill Chain
The Meta approach starts from the assumption that despite the asynchronous nature of attacks, there are still meaningful commonalities, especially where those commonalities can be abstracted from the platform or hardware being attacked. For Meta, it is the human element of the attack that is key.
Six guiding principles were used in its development: ‘observation-based’ (not designed to track hypotheses, such as assumed strategic goals); ‘tactical’ (designed for tactical analysis, not for organic social movements); ‘platform agnostic’ (suitable for everything from social media to smaller websites and email providers); ‘optimized for human-on-human operations’ (can be applied to machine-on-machine attacks, but is not primarily designed for them); ‘applicable to one or many platforms’ (both single-platform and multi-platform operations); and ‘modular’ (not every attacker will go through every phase of the chain).

The Meta kill chain, says the white paper, provides “an analytic framework that is designed to be applied to a wide range of online operations – especially those in which the targets are human. These include, but are not limited to, cyberattacks, influence operations, online fraud, human trafficking, and terrorist recruitment.”
But is also designed to be of use to a wide number of defenders, including corporate security teams, independent researchers, and law enforcement agencies. On a smaller scale, security teams may include effectively siloed response groups. Each of these defenders will be adept at discovering different links in the overall chain, but not necessarily combining all the links into a single observable chain. By providing a complete chain with a consistent taxonomy and encouraging data sharing (within privacy constraints) between the different stakeholders, Meta believes cyber defenders will learn more about attacks, campaigns, attack groups, and attack purposes – and be better able to disrupt those attacks.
As a result, the Meta kill chain contains more phases (ten) than the original Intrusion Kill Chain (seven). Two new phases, for example, are included before Lockheed Martin’s reconnaissance phase: acquiring assets, and disguising assets. These phases are more likely to be detected by independent researchers, law enforcement agencies and dark web monitoring firms than by corporate security teams – but are nevertheless part of the overall attack chain.
The full list of the ten phases of the kill chain comprises:
- Acquiring assets
- Disguising assets
- Gathering information
- Coordinating and planning
- Testing platform defenses
- Evading detection
- Indiscriminate engagement
- Targeted engagement
- Compromising assets
- Enabling longevity
Each of the phases is discussed and explained within the white paper, with copious real-life examples. Three well-documented and understood security incidents are used to demonstrate the application of the chain to actual events. These are the DCLeaks operation, the PeaceData episode, and the anti-vaccine harassment movement that Meta took down in 2021 (also known as ‘V_V’).
“Using this model,” says Meta, “allows investigators at Meta to analyze individual operations and identify the earliest moments at which they can be detected and disrupted. It will also enable them to compare multiple operations across a far wider range of threats than has been possible so far, to identify common patterns and weaknesses in the operation.”
But it transcends Meta alone. “Our goal is for this new kill chain framework to allow different investigative teams across industry, civil society, and government to share and compare their insights into operations and threat actors according to a common taxonomy, giving each a better understanding of each threat and a better chance of detecting and disrupting it.”
Related: DHS Uses Cyber Kill Chain to Analyze Russia-Linked Election Hacks
Related: Snapping Links in the Kill Chain: Lessons Learned from a Stealth Pilot
Related: The Intruder’s Kill Chain – Detecting a Subtle Presence
Related: Breaking the Cyber Kill Chain
















