McAfee recently released its quarterly threats report for Q1 2012, detailing the increase in malware across all platforms. According to the data, PC-based malware hit a new high during the quarter, making it the largest jump the segment has seen in four years.
Within the first quarter of 2012, McAfee Labs detected 8 million new malware samples, Vincent Weafer, senior vice president of McAfee Labs said.
“The same skills and techniques that were sharpened on the PC platform are increasingly being extended to other platforms, such as mobile and Mac; and as more homes and businesses use these platforms the attacks will spread, which is why all users, no matter their platforms, should take security and online safety precautions.”
Mobile users became a fresh source for criminals in Q1, McAfee notes. The threats report says that mobile-based malware surged during the quarter to the tune of nearly 8,000 new samples. When compared to the 600 samples collected in Q4 2011, the jump represents a 1200% change. A majority of the mobile threats centered on Android, but originated from third-party app stores, providing another reason for users to stick to Google Play for their application needs.
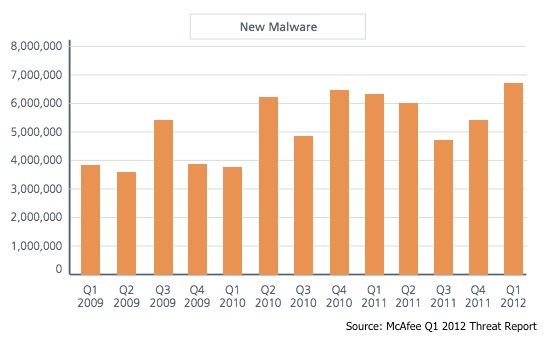
When it comes to the rise of malware on the PC, McAfee said that most of the new samples on Q1 sourced from Rootkits, password stealing Trojans. The most common delivery method and originating attack source was email. This is an interesting correlation as spam levels dipped globally in Q1 2012.
Botnet infections climbed during the quarter as well, reaching nearly 5 million infections. Of all the botnets that were active in Q1 2012, Cutwail took the top spot with 2 milliion new nodes.
Finally, based on data collected from the McAfee Global Threat Intelligence network, the United States was the primary source of SQL-injection attacks and cross-site scripting attacks, in addition to having the highest number of victims of both attacks.
The U.S. currently houses the most botnet control servers, and the location point for the vast majority of new malicious websites, with an average of 9,000 new bad sites recorded per day.
A copy of the full report is available here as a PDF download.
















