Thousands of Citrix NetScaler ADC and Gateway instances remain unpatched against a critical vulnerability that is being widely exploited, security researchers warn.
The flaw, which had been exploited as a zero-day since August, is tracked as CVE-2023-4966 (CVSS score of 9.4) and is now referred to as ‘Citrix Bleed’. It allows unauthenticated attackers to leak sensitive information from on-prem appliances that are configured as an AAA virtual server or a gateway.
Citrix released patches for the bug on October 10 and warned last week that threat actors are actively exploiting the vulnerability in the wild to perform session hijacking, which allows them to completely bypass authentication, including multi-factor authentication protections.
Over the past few days, security researchers have started raising the alarm on CVE-2023-4966 being widely exploited, with multiple threat actors, including ransomware groups, targeting internet-accessible NetScaler ADC and Gateway instances.
The ongoing mass exploitation started around the same time Assetnote published a technical writeup of the vulnerability and a proof-of-concept (PoC) exploit for it.
According to security researcher Kevin Beaumont, however, the mass exploitation has not necessarily been triggered by the PoC publication, as “it was clear multiple groups had already obtained technical details”.
By exploiting the vulnerability, attackers gain memory access to NetScaler ADC and Gateway appliances, which allows them to extract session cookies and attempt to bypass authentication. This means that even patched instances are at risk of exploitation, as the session tokens persist in memory.
The compromised cookies allow the attackers to replay the sessions for authentication. All they need to do is type ‘aaaaaaaaaaaaaaaaaaaaaaaa’ until they are in, Beaumont says.
“This cookie is issued post-authentication, which can include multi-factor authentication checks. An attacker with access to a valid cookie can establish an authenticated session to the NetScaler appliance without knowledge of the username, password, or access to a multi-factor authentication token or device,” Google’s cybersecurity arm Mandiant explains.
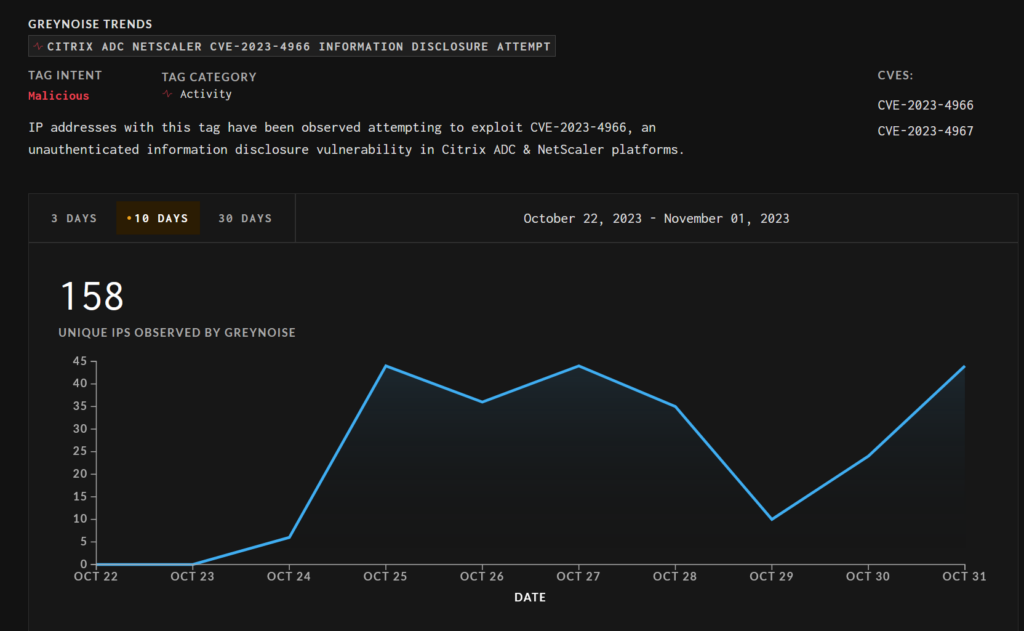
Over the weekend, Beaumont warned that attackers had stolen the session tokens of over 20,000 exploited NetScaler servers. As of November 1, data from Greynoise shows 158 unique IP addresses being used to target vulnerable instances over the past 10 days.
Warning that roughly half of NetScaler customers have yet to apply the patches, including telecommunication, electric, food, and government organizations, Beaumont last week published a scanner to help identify vulnerable NetScaler servers.
To fully address the issue, organizations should apply the available patches and then kill all active and persistent sessions, Citrix pointed out last week, underlining that there are no known workarounds or mitigations beyond these recommended actions.
“If you are using an affected build, we urge you to install the recommended updates immediately, as this vulnerability has been identified as critical. We are aware of targeted attacks in the wild using this vulnerability,” the tech giant said.
On Tuesday, Mandiant said it is currently tracking four threat actors actively targeting CVE-2023-4966, compromising NetScaler servers, and performing various post-exploitation activities.
Threat actors have deployed various tools for reconnaissance and credential theft, remote monitoring and management (RMM) tools for persistent access, a backdoor called FreeFire, living-off-the-land binaries, and utilities for lateral movement, Mandiant said.
According to Mandiant, because NetScaler does not log requests associated with the bug, organizations can hunt for exploitation attempts using “web application firewalls (WAF) or other network appliances that record HTTP/S requests directed toward the NetScaler ADC or Gateway appliances”.
The cybersecurity firm has published comprehensive instructions on how organizations can identify evidence of session hijacking, along with indicators-of-compromise (IoCs) to aid hunters.
Mandiant has seen attacks targeting government, legal and professional services, and technology organizations in the Americas, EMEA, and the APAC regions.
“Given the widespread adoption of Citrix in enterprises globally, we suspect the number of impacted organizations is far greater and in several sectors,” it noted.
Related: US Gov Expects Widespread Exploitation of Atlassian Confluence Vulnerability
Related: In-the-Wild Exploitation Expected for Critical TeamCity Flaw Allowing Server Takeover
Related: Live Exploitation Underscores Urgency to Patch Critical WS-FTP Server Flaw














