A report published this week by US-based firmware and IoT security solutions provider Finite State shows that Huawei equipment is affected by many vulnerabilities, including potential backdoors, and the company’s devices are less secure compared to the products of other vendors.
The United States and some European countries are concerned that Huawei equipment, including the one that could power future 5G networks, may contain backdoors that could facilitate spying by the Chinese government.
Huawei has denied the accusations, but it has been increasingly difficult for the company after the U.S. rolled out legislation preventing federal agencies from using Huawei products and an order signed by President Donald Trump has barred companies from using foreign telecoms equipment deemed a security risk.
While some companies and organizations, including Facebook, Google and top research universities, have started cutting ties with the Chinese telecoms giant, others have reportedly found ways to bypass the ban.
Authorities have provided little evidence to support claims that Huawei is helping the Chinese government’s spying efforts, but Finite State has decided to conduct a detailed analysis of Huawei enterprise networking products to determine what kind of risk their use poses. The company has used an automated system to analyze nearly 10,000 device firmware images created for a total of 558 products, including routers, enterprise switches, 4G LTE devices, IP phones, and blade chassis controllers.
The research found that over half of all the firmware images had at least one potential backdoor. Specifically, 29% of tested devices had at least one default username and password stored in the firmware, and 76 instances of firmware were shipped with default root user passwords that can allow backdoor access. The company also found hardcoded SSH keys, which can be useful for man-in-the-middle (MitM) attacks, in 424 firmware images.
Moreover, researchers identified, on average, 102 known vulnerabilities in Huawei firmware, mainly found in open source and third-party components. A total of nearly 9,000 critical flaws (with a CVSS score of 10) were identified across the tested firmware instances.
“Looking deeper than just the known vulnerabilities, there is substantial evidence that 0-day vulnerabilities based upon memory corruptions are abundant in Huawei firmware,” Finite State said in its report. “In summary, if you include known, remote-access vulnerabilities along with possible backdoors, Huawei devices appear to be at high risk of potential compromise.”
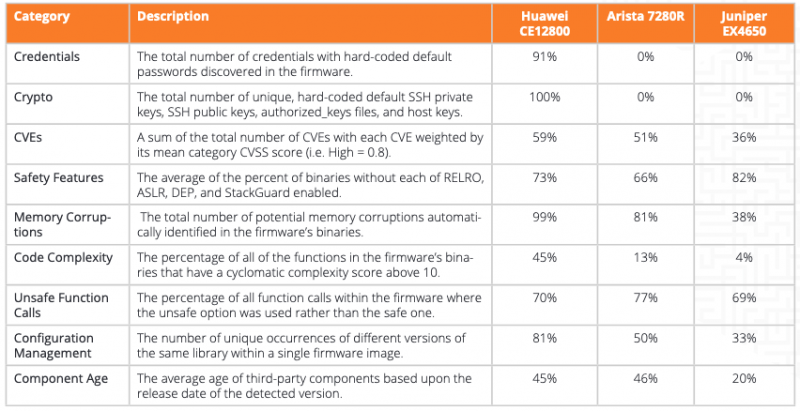
Finite State has also compared a high-end network switch from Huawei to similar products from other vendors. Specifically, it has analyzed the Huawei CE12800, the Arista 7280R, and the Juniper EX4650.
While both the products from Arista Networks and Juniper Networks had vulnerabilities, fewer issues were discovered in these devices. In some areas, such as unsafe function calls and safety features, the percentages are roughly the same. However, Finite State said it had not found any hardcoded credentials or encryption keys in the firmware of the Arista and Juniper devices, but it did find three sets of hardcoded default credentials and “numerous” crypto keys in the Huawei device.
Finite State has also made a comparison between different versions of the same firmware from Huawei in an effort to determine if security has improved over time. Researchers analyzed firmware versions v100 and v200 for the CE6851 network switch and found that the newer version actually had worse security, with a higher number of known vulnerabilities and exposed crypto keys.
“Despite Huawei’s claims about investing in security, they appear to be behind the rest of the industry in almost every respect. This overall weak security posture is concerning and obviously increases the security risks associated with use of Huawei devices,” said Matt Wyckhouse, founder and CEO of Finite State. “Whether those risks were introduced intentionally or accidentally is out of the scope of a technical assessment, and thus we cannot and do not draw any conclusions relating to intent.”
SecurityWeek has reached out to Huawei for comment and will update this article if the company responds.
UPDATE. Huawei has responded with the following statement:
We are aware of the report […] and are analyzing it. We are currently not in a position to comment on the objectiveness and integrity of the report.
Huawei welcomes any fact-based and well-intentioned suggestions that help ensure network stability. The more people who oversee and check Huawei’s products, the more likely we are to accurately identify potential issues, making our products more secure. Huawei takes cyber security very seriously, and has made it our top priority. We have not and will never implant backdoors. In addition, we will never allow anyone to do so in our equipment.
Cyber security is a technical issue that should be addressed through technical means. We will carefully analyze the report, and proactively and openly engage with the relevant parties regarding it. We welcome in-depth communication between Finite State and Huawei’s in-house security experts.
Related: Vodafone Identified Huawei Security Flaw Decade Ago













