Two dozen security advisories for the Apache Struts open source development framework have been updated after researchers determined that they contained incorrect information regarding which versions of the software were impacted by a vulnerability.
The Black Duck Security Research (BDSR) team of Synopsys’ Cybersecurity Research Center (CyRC) has reviewed 115 different Apache Struts releases and correlated them against 57 advisories covering a total of 64 vulnerabilities.
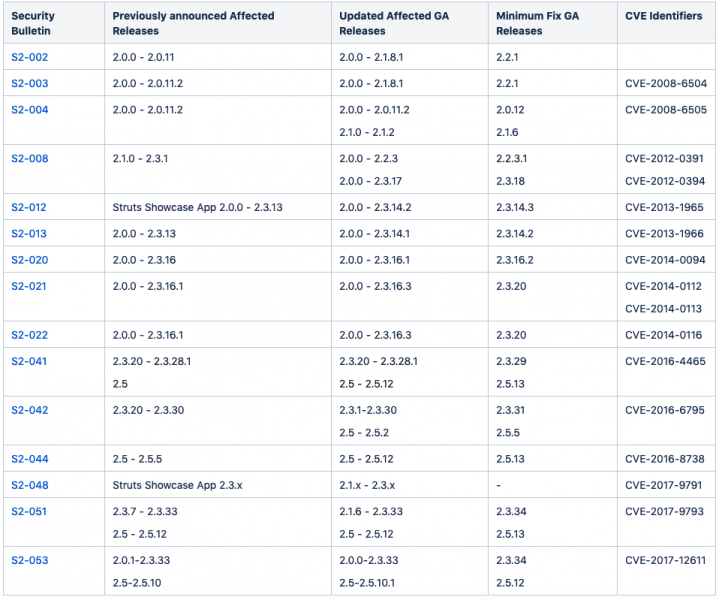
The analysis found that 24 advisories contained incorrect information about the impacted versions and 61 additional Struts versions were identified as being affected by at least one known flaw.
The updated advisories are from 2008, 2012, 2013, 2014, 2016 and 2017. For example, the initial advisory for CVE-2017-12611, a vulnerability that could allow remote code execution, initially listed versions 2.0.1-2.3.33 and 2.5-2.5.10 as being affected, but it has now been updated to say that versions 2.0.0 and 2.5.10.1 are also impacted.
A high-severity path traversal in the Convention plugin in Struts (CVE-2016-6795) was initially said to affect only versions 2.3.20 – 2.3.30, but the updated advisory lists 2.3.1-2.3.30 and 2.5 – 2.5.2.
In a few cases, the original advisory listed versions that were not actually impacted by the vulnerability.
“While our findings included the identification of versions that were falsely reported as impacted in the original disclosure, the real risk for consumers of a component is when a vulnerable version is missed in the original assessment,” said Synopsys’ Tim Mackey. “Given that development teams often cache ‘known good’ versions of components in an effort to ensure error-free compilation, under-reporting of impacted versions can have a lasting impact on overall product security.”
While none of the vulnerabilities whose advisories have been updated following Synopsys’ review appear to have been exploited in the wild, it’s not uncommon for Apache Struts flaws to be exploited in attacks. The 2017 Equifax breach, which impacted over 140 million consumers in the United States, involved an Apache Struts vulnerability that had been disclosed a few months prior to the attack.
Related: One Year Later, Hackers Still Target Apache Struts Flaw
Related: Apache Struts Flaw Increasingly Exploited to Hack Servers
Related: Oracle Products Affected by Exploited Apache Struts Flaw














