Time was when you could trust big names. Not any more – in fact ‘big names’ are increasingly targeted by the bad guys simply because we do tend to trust them. Amazon is just the latest.
Mike Olsen, co-founder of Proctorio warned Saturday that a set of security cameras he had purchased from Amazon had been infected with malware. Connecting them to a friend’s computer he didn’t quite find what he expected – they were working, but not in the way he expected.
He thought it was a bug and used developer tools to look at the code. What he found, however, was not a simple bug, an iframe linking to a website that aroused suspicions: brenz_pl/rc/.
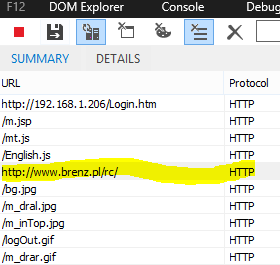 “At this point I went ahead and googled the domain, and guess what came up?” he wrote in his blog post. As long ago as March 2011, David Dede wrote on the Sucuri blog, ‘Brenz.pl is Back With Malicious iFrames’.
“At this point I went ahead and googled the domain, and guess what came up?” he wrote in his blog post. As long ago as March 2011, David Dede wrote on the Sucuri blog, ‘Brenz.pl is Back With Malicious iFrames’.
Olsen offers no suggestion that either Amazon or the supplier (Urban Security Group) are at fault in this. The cameras are Sony cameras. What it tells us, however, is that we can no longer trust a good reputation.
“Users,” confirmed Morten Kjaersgaard, CEO at Heimdal Security, “need to be aware that malware can be present in any form of device they buy.
“At the moment, fast moving consumer electronics are especially exposed. But we also saw this with Lenovo laptops and malware which was pre-installed. Cybercriminals will try to use trusted channels to get access to what they want.”
For cameras, the threat will be that installed malware could steal the data feed, while external control would mean that the property, thought to be secured, is actually made very vulnerable. Other devices could be more serious, more costly and even life-threatening.
Overall, it is an indication of the threats we must expect to increase with the internet of things. David Harley, ESET Senior Research Fellow, told SecurityWeek that while such occurrences are “very much the exception rather than the rule right now, as more and more things become connected (often unnecessarily) by vendors who haven’t really thought about the potential for security breaches via otherwise innocuous objects, it would be naïve to think that we won’t see deliberate attempts to exploit known vulnerabilities. There are already plenty of ‘Proofs of Concept’ around. Some devices may not be high-value in themselves, but usable to get to more ‘interesting’ objects.”
As an example of how easy it could be to compromise IoT devices in the modern world, Olsen told SecurityWeek, “With Amazon’s Fulfillment Service you can certainly buy these devices, load them with infected firmware and then have Amazon stock and ship them under their name/brand. Obviously Amazon isn’t scanning these devices for infections, most of them stay ‘new’ in the packaging. This could be as unsophisticated as the camera hack I found, all the way to a device with a firmware that allows remote access. People are using these things to control components in their homes, if the firmware allowed eavesdropping or remote control the possibilities are endless.”
















