Researchers believe hundreds of millions of SIM cards may be vulnerable to Simjacker attacks after determining that the targeted technology, despite being very old, is still used by at least 61 mobile operators across 29 countries.
AdaptiveMobile Security, a firm that specializes in cyber telecoms security, last month warned of a new SIM card attack method dubbed Simjacker. Simjacker involves sending specially crafted SMS messages to the targeted phone and it can be used to instruct the device to play a tone, send text messages, make phone calls, provide system information, launch a web browser, provide geographical information, and exfiltrate data.
An attacker can use Simjacker to track a user’s location, send SMS messages or make calls on the victim’s behalf, spy on users, deliver malware by opening malicious websites, and cause a denial-of-service (DoS) condition on the phone.
The Simjacker attack presented by AdaptiveMobile Security leverages a piece of legacy software still present on many SIM cards, the S@T Browser. The S@T Browser processes special SIM Toolkit (STK) instructions contained in SMS messages.
Despite not being updated since 2009, S@T Browser is still deployed by a significant number of mobile operators around the world. Tests conducted by AdaptiveMobile showed that the technology is present on SIM cards provided by at least 61 companies across 29 countries.
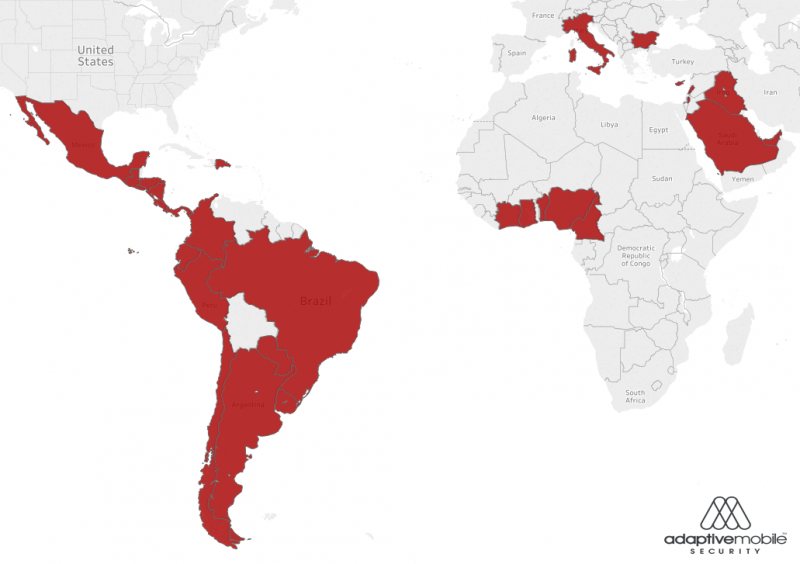
Affected regions and countries include most of South and Central America, Mexico, a small part of West Africa, Italy, Bulgaria, and the Middle East. While it’s difficult to determine exactly how many SIM cards are vulnerable to attacks, AdaptiveMobile estimates “mid to high hundreds of millions”. On the other hand, the company has pointed out that some operators may have deployed protections against these types of attacks on the network side and it’s possible that not all of their SIMs have S@T Browser.
AdaptiveSecurity says it has seen Simjacker attacks being launched in the past two years, likely by a surveillance company that offers its monitoring services to governments. A majority of the attacks were aimed at individuals in Mexico, with some exploitation attempts observed in Colombia and Peru.
The same threat actor has been known to launch attacks exploiting weaknesses in the SS7 international telecommunications standard.
“The complexity of the attacks, and the fact that it has access to multiple sources, means that it is in use by a complex, advanced entity with a wide range of skills, experience and resources. This matches the specific SS7 threat actor, who in our experience operate one of the biggest and most active SS7 attack ‘platform’ that we have observed in the world,” AdaptiveMobile said in a research paper.
The company noted, “We have more specific information on which surveillance company it could potentially be, but unfortunately, we are not able to reveal this information. To do so would reveal specific methods and information which would damage our ability to detect and block these attacks globally.”
Researchers from Ginno Security Lab recently disclosed another variant of the Simjacker attack, one involving the Wireless Internet Browser (WIB), which SmartTrust created for SIM toolkit browsing.
This method is similar to the S@T Browser attack — it allows the attacker to conduct the same type of activities and it’s also stealthy — but it’s more difficult to carry out.
However, data collected by AdaptiveMobile shows that WIB with no security mechanisms is only used by 8 operators across 7 countries in Eastern Europe, Asia, Central America and West Africa. Nevertheless, a few hundred million SIM cards may still be impacted. AdaptiveMobile says it’s not aware of any attacks targeting WIB.
Related: Many Vulnerabilities Found in Oracle’s Java Card Technology
Related: Stolen SIM Card Keys Could be Powerful Spy Tool
Related: Critical Flaw Exposes Mobile Devices, Networks to Attacks














