A new variant of a recently disclosed SIM card attack method could expose millions of mobile phones to remote hacking, researchers have warned.
Earlier this month, cyber telecoms security firm AdaptiveMobile Security disclosed the details of Simjacker, an attack method that involves sending specially crafted SMS messages to the targeted mobile phone.
The attack relies on the fact that these special messages are processed by the legacy S@T Browser present on many SIMs. An attacker could issue commands to conduct various types of activities, including sending SMS messages, making phone calls, launching a web browser, and collecting information about the targeted device, regardless of operating system and manufacturer.
AdaptiveMobile estimated that the attack could work against over 1 billion mobile phones considering that the S@T Browser is present on SIM cards provided by mobile operators in more than 30 countries. The company also claimed that an unnamed organization that helps governments monitor individuals has been using this method for at least two years.
The Simjacker attack method that leverages the S@T Browser was also independently discovered by researchers at Ginno Security Lab, a non-profit cybersecurity organization. Ginno Security Lab has dubbed the method S@Tattack and recently published a blog post describing its findings.
However, Ginno Security Lab has also identified a second SIM card attack method, one that involves the Wireless Internet Browser (WIB), which SmartTrust created for SIM toolkit based browsing. This attack has been dubbed WIBattack.
Similar to the S@T Browser, WIB can be controlled remotely with Over the Air (OTA) SMS messages, which are typically used by mobile operators to provision or change core network settings on a device.
Similar to the S@T Browser attack, a malicious actor could abuse WIB to conduct various activities on a mobile device using specially crafted SMS messages. An attacker can display arbitrary text or an icon on the screen on top of everything else, launch a browser and have it access a specified URL, provide location information, send SMSs, and make phone calls.
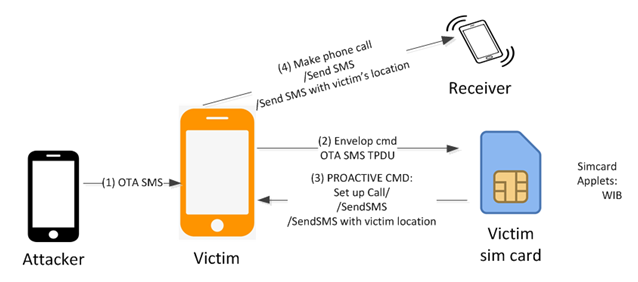
Both attacks are difficult to detect and stealthy — there is no indication to the victim that their device has been targeted.
However, Ginno Security Lab’s chief researcher, who uses the online moniker Lakatos, told SecurityWeek that more knowledge is needed to exploit WIB compared to the S@T Browser due to the fact that the WIB specification is not documented.
“The process for the researchers to find bytecode/payload of OTA SMS to attack the WIB browser is more difficult than S@T Browser,” Lakatos explained.
The researcher said they discovered these vulnerabilities back in 2015, but the details were kept secret due to the fact that they are very difficult to patch and relatively easy to exploit.
“If the attacker knows one network does not filter OTA SMS, he can launch mass attacks targeting a large number of subscribers of the network,” he noted.
“We are now focusing on finding solutions to protect people against the threats of backdoor applications in SIM cards. We should find a solution to protect subscribers even if we don’t need to know in detail what applications exist in SIM cards,” Lakatos said. “And we are developing a SIM-scanning application that can run on Android OS to help many people who want to know if their SIM card is safe from WIB and S@T or not. We will publish the application on Google Play when we finish it soon.”
In addition to the blog post, Ginno Security Lab created a video showing how the WIBattack works:
Ginno Security Lab has reported its findings to the GSM Association (GSMA), which represents mobile network operators worldwide. GSMA has confirmed for SecurityWeek that it has been made aware of the WIBattack and S@Tattack attacks affecting some SIM cards.
“We are considering the research and its impact with our mobile industry partners and are grateful to the researchers for affording the industry the opportunity to consider their findings,” GSMA said in an emailed statement. “This research is similar to other research recently sent to us under the name ‘Simjacker’. The GSMA has worked with the mobile industry to create guidance for operators and SIM manufacturers to deal with ‘Simjacker’, including how to identify which SIMs are impacted and on ways to mitigate the issue. The GSMA is working with the mobile industry to proactively identify and fix similar issues in other legacy SIM technology.”
GSMA added, “The GSMA welcomes any research that enhances the security and user confidence of mobile services and encourages all researchers to submit their work to our Coordinated Vulnerability Disclosure (CVD) Programme which enables them to share findings and to contribute to industry’s ongoing work to drive security improvements.”
Related: Many Vulnerabilities Found in Oracle’s Java Card Technology
Related: Stolen SIM Card Keys Could be Powerful Spy Tool
Related: Critical Flaw Exposes Mobile Devices, Networks to Attacks














