An increasing number of companies in the industrial sector have experienced a targeted attack, according to a survey conducted by Kaspersky Lab and B2B International.
As part of its 2017 IT Security Risks Survey, Kaspersky talked to more than 5,200 representatives of small, medium and large businesses in 29 countries about IT security and the incidents they deal with.
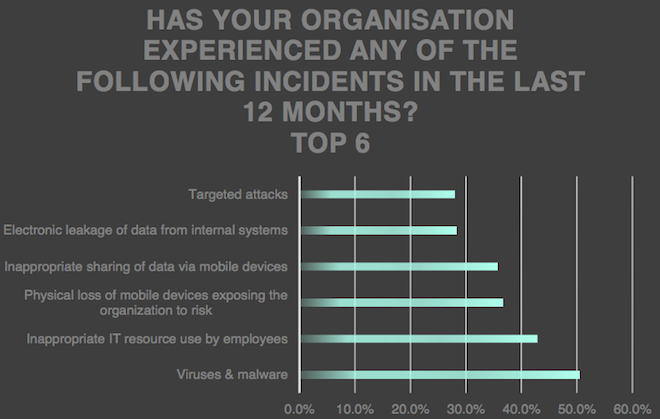
Of the 962 industrial companies surveyed, 28% said they had faced a targeted attack in the last 12 months. This represents an 8 percentage point increase compared to the previous year.
“The fact that the most dangerous incident type has grown by more than a third strongly suggests that cybercriminal groups are paying much closer attention to the industrial sector,” Kaspersky said.
More than half of industrial organization surveyed by Kaspersky reported being hit by malware attacks in the last year.
A majority of industrial sector respondents claimed that the security incidents they experienced were complex, and nearly half admitted that there is insufficient insight into the threats they face.
Roughly one-third of companies reported that it had taken them several days to detect an incident, while 20% said it had taken them several weeks.
While 62% believe sophisticated security software is necessary to address potential threats, almost half of respondents also noted that staff has not followed IT security policies. The number of people who blamed staff in the industrial sector is 6% higher compared to other sectors that took part in Kaspersky’s survey.
“Cyberattacks on industrial control systems have become the indisputable number-one concern. The good news is that the majority of industrial market players know which threats are coming to the fore today and will be relevant in the near future,” explained Andrey Suvorov, Head of Critical Infrastructure Protection Business Development at Kaspersky.
“That’s why it’s crucially important to implement a complex security solution that’s specifically designed to protect automated industrial environments, is highly flexible and configured in accordance with the technological processes of each organisation.”
Related: DHS Warns of Malware Targeting Industrial Safety Systems
Related: Thousands of Malware Variants Found on Industrial Systems
Related: The Future of Industrial Security – IT and OT Convergence













