The National Cybersecurity & Communications Integration Center (NCCIC) of the U.S. Department of Homeland Security (DHS) on Monday published an analysis report on a piece of malware designed to target industrial safety systems.
FireEye and Dragos reported last week that sophisticated malware, tracked by the companies as Triton and Trisis, caused a shutdown at a critical infrastructure organization somewhere in the Middle East. CyberX, a firm that specializes in industrial cybersecurity, believes Iran was likely behind the attack and the target was probably an organization in Saudi Arabia.
The NCCIC, which dubbed the malware “HatMan,” published a report that describes the threat, and provides mitigations and YARA rules.
The Python-based HatMan malware targets Schneider Electric’s Triconex Safety Instrumented System (SIS) controllers, designed for monitoring processes and restoring them to a safe state or perform a safe shutdown if a potentially dangerous situation is detected.
The malware communicates with SIS controllers via the proprietary TriStation protocol, and allows attackers to manipulate devices by adding new ladder logic.
The attack on the critical infrastructure organization in the Middle East was discovered after the hackers’ activities resulted in the SIS controller triggering a process shutdown. However, experts believe this was likely an accident, and the final goal may have been to cause physical damage.
The NCCIC pointed out in its report that the malware has two main components: one that runs on a compromised PC and interacts with the safety controller, and one that runs on the controller itself.
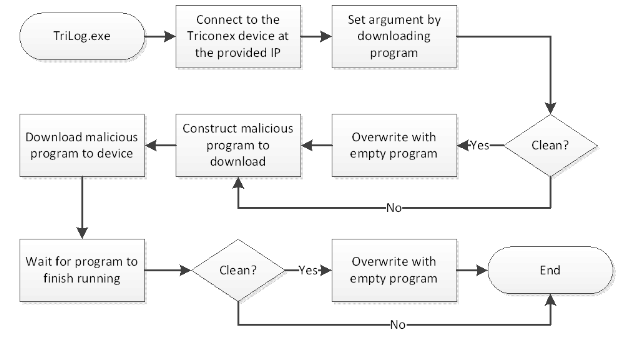
“Although by itself HatMan does not do anything catastrophic — safety systems do not directly control the process, so a degraded safety system will not cause a correctly functioning process to misbehave — it could be very damaging when combined with malware that impact s the process in tandem. Were both to be degraded simultaneously, physical harm could be effected on persons, property, or the environment,” NCCIC said in its report.
“It is safe to say that while HatMan would be a valuable tool for ICS reconnaissance, it is likely designed to degrade industrial processes or worse. Overall, the construction of the different components would indicate a significant knowledge about ICS environments — specifically Triconex controllers — and an extended development lifecycle to refine such an advanced attack,” it added.
Schneider Electric has launched an investigation into this incident. The company said there had been no evidence that the malware exploited any vulnerabilities in its products. The automation giant has advised customers not to leave the device in “Program” mode when it’s not being configured as the malware can only deliver its payload if the controller is set to this mode.
“The fact that this actor has the capability to access the safety instrumentation device, and potentially make changes to the device firmware unnoticed, should make critical infrastructure owner-operators sit up and take heed,” said Emily S. Miller, Director of National Security and Critical Infrastructure Programs at Mocana. “Yes, in this case the malware tripped the safety systems and was noticed, but who’s to say the actor won’t learn from its mistakes or hasn’t already?”
Related: Thousands of Malware Variants Found on Industrial Systems
Related: Non-Targeted Malware Hits 3,000 Industrial Sites a Yea












