Tacoma, Washington-based IID, launched a new information sharing platform this week, where government agencies and enterprises can share data about the latest threats and ongoing attacks.
Called ActiveTrust, the platform enables participating organizations to exchange threat intelligence and coordinate response between organizations.
“ActiveTrust accelerates big collaboration for actionable security intelligence by giving organizations a better way to get the security information they need; creating a dynamic, aligned and private community of security peers,” the company explained.

The ActiveTrust platform consists of three elements:
• Controlled Exchange – ActiveTrust members are prescreened and must agree to a common set of rules for confidentiality and information usage. The threat exchange platform includes data governance controls, so members can dictate what, where, when and with whom they share—even anonymously.
• Efficient Intelligence Delivery – ActiveTrust takes disparate sources of data in various formats and standardizes it, offloading the work needed to translate data and making the intelligence instantly actionable. By plugging actionable data into whatever gear organizations have, every existing security investment becomes more valuable and powerful.
• Broad-Based Collaboration – Participation in ActiveTrust gives security professionals instant access to a wealth of data from a variety of allies and peers in the security ecosystem. ActiveTrust members also have the ability to share insights and discuss best practices through various features on ActiveTrust’s social network.
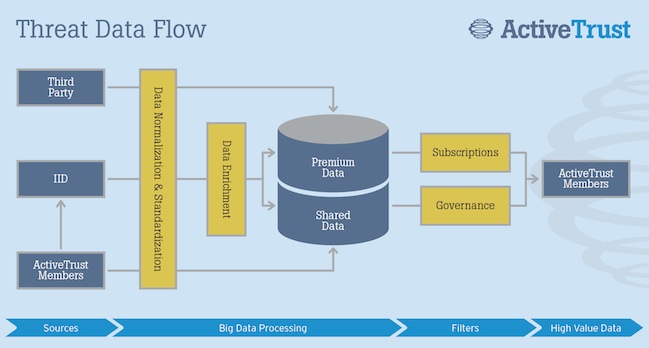
Dozens of Fortune 500 companies and U.S. government agencies are already utilizing the platform to power their existing security infrastructure, IID said.
“Much like cybercriminals have leveraged intelligence exchanges to carry out their attacks, ActiveTrust provides the ‘good guys’ with their own sharing networks to gather information vital to fending off attacks,” said IID CEO Lars Harvey. “IID has spent more than ten years making connections between organizations to secure their networks, so it’s only logical that we are launching a threat exchange platform that makes it faster, easier and more efficient than ever for organizations to identity and defend themselves against cyberattacks.”
ActiveTrust is priced at $300,000 per year for a large enterprise subscription.
In November 2013, IID, also known as “Internet Identity”, announced that it has raised $8 million in Series A funding from Bessemer Venture Partners.
Additional information on ActiveTrust is available here.












