Many security practitioners in the field of industrial control systems (ICS) believe the level of risk is high, and they are increasingly concerned about ransomware and embedded controllers, according to the SANS Institute’s fourth annual ICS cyber security survey.
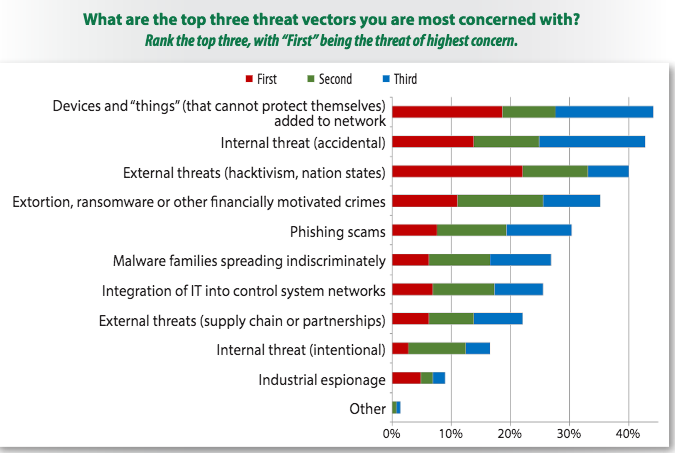
ICS security experts from organizations of all sizes told SANS that they believe the top threat vectors are devices that cannot protect themselves, such as embedded controllers (44%), internal threats, including accidents (43%), external threats, such as nation-state actors and hacktivists (40%), and ransomware and other extortion attempts (35%).
Ransomware has made a lot of headlines in the past year and industrial systems are at risk, as demonstrated by both theoretical attack scenarios and in-the-wild threats such as the WannaCry malware. As a result, the number of ICS security experts concerned about ransomware has nearly doubled compared to data from the previous SANS survey.
“Although ransomware primarily infects commercial OS-based systems (e.g., Windows, Linux), the integration of these into ICS environments and the dependence of ICS on devices running these operating systems has extended ransomware’s effectiveness and reach,” SANS said in its report. “Publicly known operational impacts remain few to date but, we expect more to follow, especially given public demonstrations of ransomware targeting ICS/SCADA.”
Recent ICS hacking demonstrations also appear to have contributed to an increasing awareness that embedded controllers and control system applications are at risk – nearly one-quarter of respondents believe controllers are most at risk. On the other hand, many still believe that computers running commercial operating systems are most at risk and have the greatest impact.
More than two-thirds of respondents believe the threat to ICS to be high or critical, and nearly half said their budgets for ICS security increased from the fiscal year 2016. Over the next 18 months, 20 percent or more of organizations have allocated budget for performing security assessments or audits of control systems, increase visibility into these systems, increase security awareness training, and implement anomaly and intrusion detection tools.
“Budgets for training and certification of staff responsible for implementing and maintaining security of control systems and control fell considerably, from 34% in 2016 to 26% in 2017. Rather than balancing this with increases in trained staff or outside consultants, budgets for these initiatives decreased, dropping, at 14%, below the top 10 budgetary initiatives,” SANS said. “At a time of increasing exposures and risk factors, this is counterintuitive. Rising threat levels and expanding attack surfaces require skilled professionals to address these risks.”
Of the organizations with more than 10,000 employees, 2.6 percent said they have a budget of more than $10 million for control system security in the fiscal year 2017, and 6 percent said they have a budget ranging between $1 million and $10 million. On the other hand, 2.6 percent of large companies admitted they don’t have a budget for ICS security.
The fact that some organizations have allocated budget for improving visibility is encouraging, considering that when asked if their control systems have been infected or infiltrated, 40 percent of respondents said “not that we know of,” which suggests they may have been breached, but lack visibility into their operational technology (OT) network.
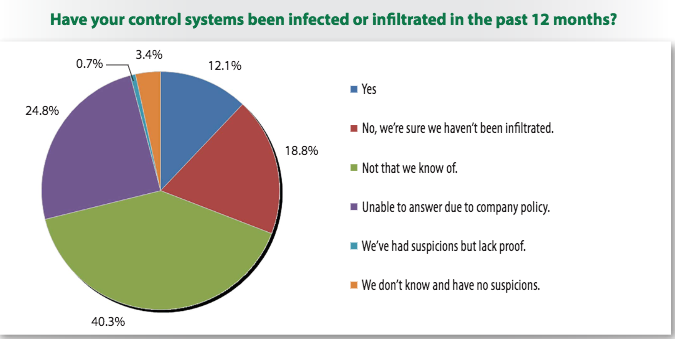
Roughly 12 percent of respondents said their control systems were infected or infiltrated in the past year. While most of them either did not know how many times their systems were breached or said they had only detected such events up to five times, some reported more than 50 incidents.
Related Reading: Non-Targeted Malware Hits 3,000 Industrial Sites a Year
Related Reading: Group Pushes For Industrial Control Systems (ICS) Security Testing Standards
Related Reading: IBM Reports Significant Increase in ICS Attacks













