Threat intelligence company Digital Shadows has uncovered over 550 fake domains attempting to mimic websites related to the 2020 presidential election in the United States.
The company’s researchers identified typosquatted domains targeting Democratic and Republican candidates, along with funding sites of the Republican Party.
Roughly one-third of the typosquatted domains are either non-malicious, which means they host no content or content that only makes fun of a candidate, or they are misconfigured or unauthorized websites, which includes improperly configured sites that only host an index page and unofficial domains that may have been set up by fans of a candidate.
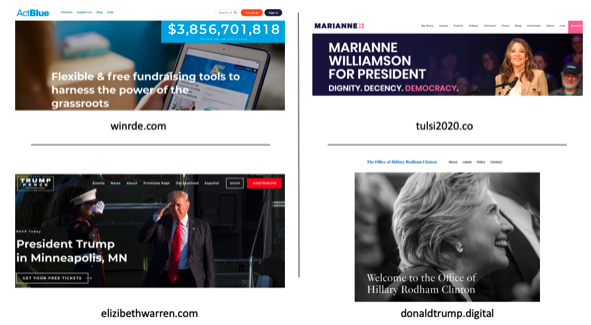
The rest, however, representing 68%, redirect visitors to other sites, in many cases ones belonging to the competition. For example, the winrde.com domain, which may be accessed by users who want to go to the Republican donation website WinRed.com, redirects users to ActBlue, the primary fundraising website of the Democrats.
The domains tulsi2020.co and elizibethwarren.com — the legitimate domains are tulsi2020.com for Tulsi Gabbard and elizabethwarren.com for Elizabeth Warren, both Democratic candidates — redirect visitors to marianne2020.com and donaldjtrump.com, the campaign websites of Democratic candidate Marianne Williamson and Republican candidate Donald Trump.
Six of the fake election domains have been found to redirect visitors to websites offering file conversion and secure browsing Chrome extensions. Some of these tools can allow attackers to hijack users’ browser sessions.
In one case, researchers uncovered an IP address hosting over 60 fake domains, including a dozen related to candidates or political topics. All of the domains were registered to an address in Panama, with other information hidden by the WhoisGuard privacy protection service.
“Setting up a fake domain is easy with virtually no checks from the organization selling the address. It’s easy for malicious actors to dupe voters and just as easy to impersonate brands and companies to commit fraud. It’s a problem we see every day,” said Harrison Van Riper, research analyst at Digital Shadows.
“An unintentional consequence of GDPR since the regulation’s enactment last May has been the removal of domain registration details from the official records making it very hard to tell who or what organization stands behind a specific domain,” Van Riper added.
“Data from June 2018 to June 2019 indicates that brand protection providers have had only 4% to 14% of Whois reveal requests actioned successfully. GDPR has generally been a great initiative, but in terms of domain impersonation, it’s had unintended consequences that aid criminals and other actors that are out to cause confusion and harm,” he explained.
Related: 2020 U.S. Presidential Candidates Vulnerable to Email Attacks














