
Hacktivists might not know a lot about industrial control systems (ICS), but they’re well aware of the potential implications of these devices getting compromised. That is why some groups have been targeting these systems — which are often unprotected and easy to hack — to draw attention to their cause.
Industrial cybersecurity firm Otorio reported in early September that a pro-Palestine hacktivist group named GhostSec had claimed that it ‘hacked’ 55 Berghof programmable logic controllers (PLCs) located in Israel. The hackers published a video showing that they had access to the PLC’s administration panel and an associated human-machine interface (HMI). They also posted a screenshot showing that a PLC had been stopped, which, for someone who doesn’t know much about how industrial processes work, might indicate that significant disruption may have been caused.
Roughly one week later, Otorio saw the same hacktivists taking credit for another attack on Israeli ICS, this time claiming to be able to control parameters related to water safety.
In the case of the incident involving Berghof PLCs, the security firm’s researchers showed that it’s easy to identify the internet-exposed PLCs using the Shodan search engine and found that many can likely be accessed using default or common credentials. The researchers determined that while the compromised PLC admin panel does provide full control over some functionality, it does not allow a user to directly control the industrial process.
“It is possible to affect the process to some extent, but the actual process configuration itself isn’t available solely from the admin panel,” Otorio explained.
The company has also analyzed GhostSec’s second round of claims and found that the water-related ICS was actually associated with a hotel’s pool.
Otorio researchers told SecurityWeek that the hacktivists apparently claimed to have breached a system that is more important than the HMI of a hotel pool — they likely thought the pH and chlorine parameters were associated with drinking water. The experts noted that without conducting their analysis, it would have been difficult to tell that the ICS is associated with a pool.
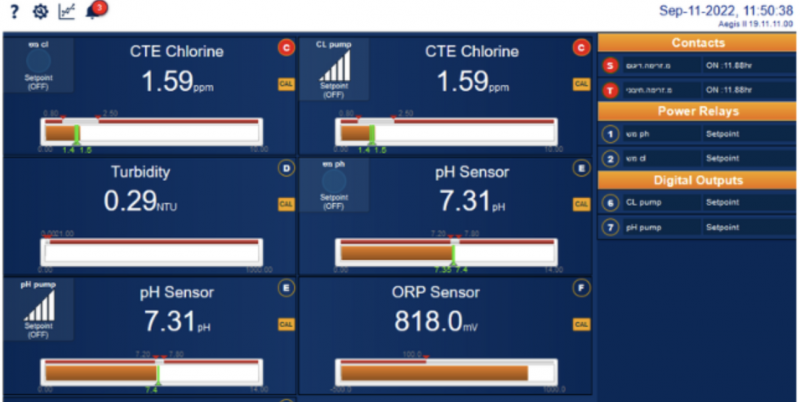
On the other hand, based on their observations, an attacker could not only monitor, but also modify those parameters, which could pose a health risk to individuals using the pool.
While believing that they had gained access to systems that could be used to control drinking water parameters, the hackers said they would not alter any settings to prevent causing harm to people in Israel as that would go against their mission and beliefs.
SecurityWeek has talked to several experts from industrial cybersecurity firms to find out what they think about the threat posed by hacktivists to ICS. How far could they go based on their skills and knowledge, and how far would they go?
It’s well known that ICS is often exposed to the internet and in many cases these systems can be easily accessed via insecure configurations, vulnerabilities, and widely available tools.
The U.S. government issued a warning to organizations about hacktivists being able to easily target industrial systems nearly a decade ago.
There have been several incidents apparently involving hacktivists and ICS over the past years. In 2020, an Iranian group accessed systems at a water facility in Israel.
More recently, a group named ‘Gonjeshke Darande’ took credit for causing disruptions in Iran, including forcing a steel company to halt production and paralyzed gas stations across the country. They claimed the attacks were in response to Iran’s aggression.
However, in the case of some attacks, particularly such as the ones that hit Iran, some experts believe they could be false flags — attacks launched by a nation state actor under the guise of hacktivism.
Learn more about threats to industrial control systems at
SecurityWeek’s 2022 ICS Cyber Security Conference (agenda is now available)
Michael Langer, chief product officer at Radiflow, pointed out that groups operating under political or military interests — even if they do not have state resources at their disposal — should not be considered hacktivist groups. One example is Gaza Cybergang, which has been linked to Hamas.
Langer defined hacktivists as “politically motivated but mostly unorganized and not financially sponsored/motivated people” and “someone who is looking for an easy opportunity to exploit poorly protected networks and therefore to demonstrate to the world a specific message”.
Langer says hacktivists have moderate cyber sophistication, focusing on unprotected ICS or IoT devices that are exposed to the internet. They typically rely on open ports, publicly available tools, and they typically operate for short periods of time to achieve a specific goal.
“Sometimes they probably will choose their targets based on ease-to-compromise criteria and not necessarily by relevance to their goals. For example, searching on Shodan for some exposed devices from a specific vendor and trying hard-coded default credentials to establish presence on that device,” Langer explained.
“Most of the targets will probably be distributed networks or sites which heavily depend on remote access (for maintenance, vendor monitoring, etc), like water facilities, building management systems, industrial segments of municipal networks or SMB networks (like pools, traffic lights, restaurants),” he added.
What could hacktivists achieve when targeting ICS?
“Although hacktivist cyber activities may cause mainly localized disruption and other effects, as the current status of ICS cyber security stays relatively bad, exploiting frequent device misconfigurations, non-enforced 3rd party access and other basic security weaknesses by these hackers can also lead to major consequences jeopardizing public safety,” Langer said.
David Krivobokov, security researcher at Otorio, commented, “The fact that operational, ICS systems are connected directly to the internet without any proper security measures, really lowers the bar to these kinds of threats, which makes it more effective to exploit OT infrastructure in order to scare the public rather than defacing a website. Moreover, the potential damage for an attacker that is logged into one of these systems is no less than catastrophic in many cases. If their goal is to scare the public, they are doing exactly what I would do if I were them.”
One interesting aspect is pointed out by Danielle Jablanski, OT cybersecurity strategist at Nozomi Networks.
“There may be cognitive dissonance and compartmentalization of activities that go on in organized hacktivist campaigns where individuals may think they are doing something small or negligible, but in reality, it turns out to have catastrophic impacts. This is heightened when it comes to altering physical processes and controls for the products, services, and resources we rely on to sustain day to day life,” Jablanski explained.
She noted that the hackers in the recent examples seen by Otorio are likely unfamiliar with OT.
“My concern is when individuals close that knowledge gap, how much more leverage will they have in these types of activities. As an industry we don’t know the exact threshold for the amount of available data and access that will lead to widespread exploitation of process control systems,” Jablanski said.
She added, “Despite the intent and consequences of targeting ICS, many processes have contingencies and have failover methods in place to prevent worst case scenarios from happening. I do think the capability to disrupt and degrade the process control system poses a significant societal risk. It really is a matter of when, not if, more ICS incidents occur.”
Sharon Brizinov, director of security research at Claroty, noted that in some cases it’s enough for a threat actor to “claim access to critical infrastructure in order to gain attention, demonstrate technical capabilities, and claim some sort of political victory”.
“Nonetheless, asset owners and operators should not take hacktivists lightly. The potential for disruption exists given the type of access a group may obtain, and there’s nothing stopping a hacktivist from turning into an extortionist and claiming to have stolen data or threatening to infect critical IT systems with ransomware, for example,” Brizinov said.
Thomas Winston, director of intelligence content at Dragos, said hacktivist attacks on ICS are often small in scope — they can cause temporary loss of view and potentially loss of control. However, even such a temporary or limited incident could present serious challenges to, for instance, water organizations, and impact public confidence on the safety of the water.
On the other hand, Winston noted, “There are always exceptions to everything but to achieve extensive long-term disruption to the steady state operations of the plant will often require ICS/OT knowledge and access to non-windows ICS/OT devices.”
Winston pointed out that disruptive attacks on ICS require significant resources, including in terms of money, research and personnel. However, he said it’s common to see adversaries targeting enterprise IT networks and accidentally discovering a connected or poorly segmented OT network.
“In the Kemuri Water Company breach from 2016, we saw a hacktivist adversary target and attack the enterprise IT of Kemuri, exploiting known IT vulnerabilities, and doing this they discovered the unprotected OT administrative credentials,” Winston said.
Ron Fabela, CTO & co-founder at SynSaber, said there is an increasing trend of hacktivists, cybercriminals and vendor researchers targeting ICS. One recent example involves the Cl0p ransomware gang targeting the South Staffordshire water company in the UK, and claiming to gain access to SCADA systems.
“Interested parties will often use tools such as Shodan to ‘discover’ ICS screens on the internet. These screenshots are posted online in order to gain notoriety and perhaps shame the target organization, but rarely are any impacts executed or announced,” Fabela said. “Now even vendor research teams are making overblown claims about vulnerabilities found within ICS devices or software in order to increase traffic and attention, but stop short of proving the viability of such exploitation in the real world.”
Fabela added, “What these examples share is a lack of executing the final step in an ICS hack: acting on objectives to disrupt the process. Most cases of ‘ICS’ security events are not actually direct attacks on the control systems themselves. Whether it’s a group that ransoms the IT network of a control system organization, someone on social media posting HMI screens for fun, or security vendor marketing gone too far, universally, no one wants to be responsible for the impact of actual disruption of operations.
“Perhaps as a result of this ‘red line’ that few but nation-states are willing to cross, claims tend to be overblown with ridiculous ‘what if’ statements about impact that never happen. While it’s nearly impossible to determine an adversary’s exact intention, we in the community hope that an increased interest in industrial control system security continues to stop short of process disruption.”
What should organizations do?
“These attacks can be easily mitigated by securing internet access, hardening authentication mechanisms, performing basic ICS security monitoring by a chosen MSSP, enforcing basic cyber security hygiene, etc,” Langer said.
“Enterprises should prepare themselves for that and more substantial threats by performing regular cyber risk assessment not just in IT networks but also through OT segments with consideration to actual business and environmental importance,” he added.
Related: Hacktivists Leak Data Allegedly Stolen From Russian Energy Giant Transneft
Related: Belarus Hacktivists Target Railway in Anti-Russia Effort














