A group of cybercriminals that breached the systems of Japanese video game giant Capcom is demanding $11 million after deploying ransomware and stealing vast amounts of data.
Capcom, which has operations in the US, Europe and East Asia, is best known for games such as Resident Evil, Street Fighter, Devil May Cry, Monster Hunter, Ace Attorney and Mega Man.
The company revealed on November 4 in a press release that it detected unauthorized access to its internal networks a couple of days earlier. Capcom said it was forced to halt some operations and that the incident impacted its email and file servers, among other systems. It claimed that it had found no evidence of customer information being compromised.
However, the cybercriminals who breached Capcom, a group that uses the ransomware known as Ragnar Locker, claim to have stolen more than 1 TB of files, including accounting files, banking statements, financial reports, tax documents, intellectual property, proprietary business information, personal information of employees and customers, corporate contracts, emails, private chats, and various other types of information.
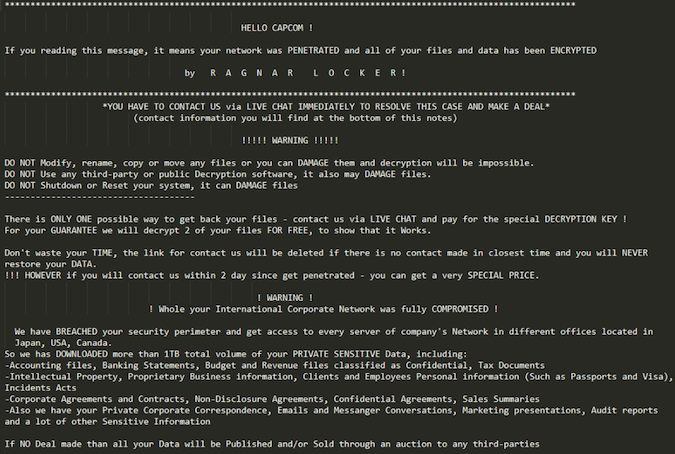
A researcher who uses the online moniker pancak3 told SecurityWeek that he learned from the attackers that they are initially asking Capcom to pay $11 million in bitcoin.
The researcher says the hackers claim their ransomware encrypted roughly 2,000 Capcom servers, including file servers. The attackers have posted some screenshots to prove that they’ve gained access to sensitive information.
Ragnar Locker operators demanded a similar ransom from renewable energy company EDP, whose systems they breached in May. The same ransomware is also believed to have been involved in recent attacks targeting the United Nations’ International Maritime Organization and French shipping giant CMA CGM.
Related: University Project Tracks Ransomware Attacks on Critical Infrastructure
Related: IT Services Giant Sopra Steria Hit by Ransomware
Related: Toy Manufacturer Mattel Discloses Ransomware Attack















