Vulnerabilities in business applications and industrial processes can expose companies in the oil and gas sector to high-impact cyberattacks, researchers have warned.
In a presentation at the Black Hat security conference in Amsterdam, researchers from ERPScan, a company that specializes in securing SAP, Oracle and industry-specific business applications, demonstrated how an organization’s most critical systems can be accessed by malicious actors exploiting vulnerabilities in business applications.
Vulnerabilities in the bridge between IT and OT
Critical infrastructure is increasingly targeted by malicious cyber actors and while such systems are in many cases considered secure by their operators, experts and recent incidents have demonstrated that the threat is real.
SCADA applications are usually deployed on a dedicated operational technology (OT) network that is separated from the corporate network and the Internet by a firewall. However, as IT and OT have started to converge, there are an increasing number of software solutions that provide a bridge between these two environments, including systems used for enterprise resource planning (ERP), enterprise asset management, manufacturing integration, project portfolio planning, and laboratory information management (LIMS)
According to ERPScan’s Alexander Polyakov and Mathieu Geli, there are multiple ways in which malicious actors can gain unauthorized access from the corporate network to the operational network by leveraging software vulnerabilities and improper configurations.
Products such as Oracle’s E-Business Suite, the SAP HANA relational database management system, SAP Plant Connection (SAP PCo), which is used for data exchanges between a SAP system and industry-specific data sources, SAP Manufacturing Integration and Intelligence (xMII), which provides a direct connection between shop-floor systems and business operations, and OPC servers from MatriconOPC have all been found to contain serious vulnerabilities.
Attacks against oil and gas companies
These products are used by numerous oil and gas companies — SAP reported last year that over 800 companies, including 85 percent of Forbes 2000 firms, had used its solutions for the production of more than 70 million barrels of oil per day.
Researchers say the vulnerabilities found in these products can be exploited by malicious actors in a multi-stage attack to gain access to industrial control systems (ICS) from the business network.
“For example, if you have some plant devices which collect data about oil volumes, you should somehow transfer this data to the corporate network to demonstrate it on nice dashboards managers to develop a long-term financial strategy and take decisions,” explained Polyakov, CTO of ERPScan. “That’s why even if you have a firewall between IT and OT, there are some applications which are still connected, and these connections are often insecure. So, it possible to conduct such attack and jump from IT network (or even the Internet) into OT network up to SCADA systems, OPC servers, field devices, and smart meters.”
There are several attack vectors that malicious actors can use to gain access to an organization’s corporate network. Once in, they can leverage one of the many vulnerabilities found in Oracle and SAP business-critical applications to make their way to the OT.
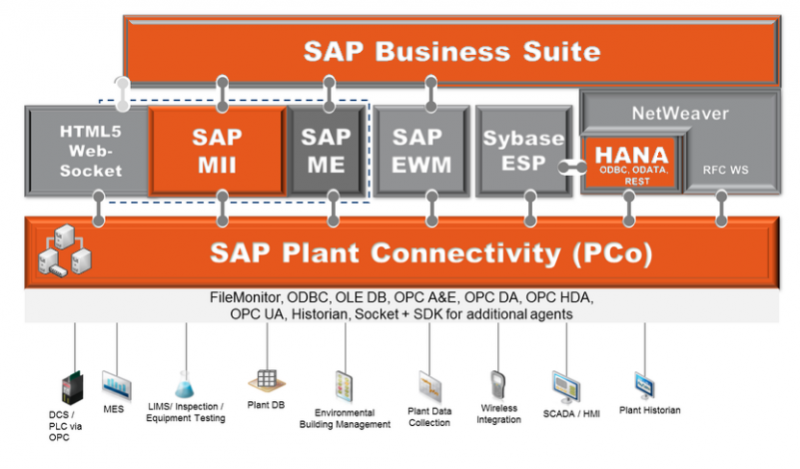
In one attack scenario described by ERPScan, the attacker gains access to a SAP ERP product, moves to SAP xMII, and from there to SAP PCo, which can give them access to SCADA systems, programmable logic controllers (PLCs), and smart meters. The attack path can also go through SAP PCo, the OPC server, and then the PLCs and field devices.
A total of more than 3,500 vulnerabilities have been discovered by researchers in SAP products. This includes SAP xMII and PCo flaws patched by the vendor this week with its November 2015 security updates.
ERPScan researchers have described several worst case scenarios that could result from cyberattacks exploiting vulnerabilities in these systems. For example, they claim an attacker could exploit vulnerabilities in SAP xMII and SAP PCo, solutions that transfer data from tank management systems to other SAP products, in an effort to alter the oil quantity information seen by managers.
“Assume that every day one sends information that there is much more oil in stock than we really have,” experts said in their Black Hat presentation. “One day the company will have sold out all the oil and won’t be able to deliver it to its customers. The failure to perform the obligations could lead to a global scandal, changes in oil prices and huge losses up to the company’s bankruptcy.”
Researchers also believe attackers could sabotage plant equipment and even cause physical damage. During their Black Hat presentation, Polyakov and Geli provided a practical demonstration of a multi-stage attack targeting an oil company.
Response from SAP
In response to ERPScan’s Black Hat presentation, SAP has provided the following statement:
“SAP Product Security Response Team collaborates frequently with research companies like ERPScan to ensure a responsible disclosure of vulnerabilities. All vulnerabilities disclosed at the European Blackhat conference (Nov. 10 -13, 2015, Amsterdam/Netherlands) have been fixed, and security patches are available for download on the SAP Service Marketplace. We strongly advise our customers to secure their SAP landscape by applying the available security patches from the SAP Service Marketplace immediately.
SAP stands for secure and reliable software solutions. As the global leader in business software, SAP takes the security of customer data seriously and has based its development processes on a comprehensive security strategy (“Prevent – Detect – React”) across the enterprise that relies on trainings, tools and processes to enable the delivery of secure products and services.”














