FireEye has released a piece of software that creates a fully customizable virtual machine (VM) containing all the tools and tweaks needed for malware analysis and other cybersercurity-related tasks.
FLARE VM – where FLARE stands for FireEye Labs Advanced Reverse Engineering – is a Windows-based security distribution inspired by Linux distros such as Kali and REMnux. It was developed by FireEye threat researcher Peter Kacherginsky in order to address the challenges associated with maintaining a custom VM.
It provides a platform that includes a comprehensive collection of security tools that can be used to conduct malware analysis, reverse engineering, incident response, forensic investigations and penetration testing. It includes disassemblers, debuggers, decompilers, static and dynamic analysis, exploitation, vulnerability assessment, and network analysis tools.
In order to install FLARE VM, users need a virtual machine with Windows 7 or a newer version of the operating system. From the VM, they need to visit a URL in Internet Explorer and the installation starts. The process takes 30-40 minutes, depending on the connection speed, and it involves several restarts of the system.
Once the installation has been completed, users are advised to make a snapshot of the VM to save its clean state and switch networking settings to Host-Only in order to prevent the analyzed malware samples from connecting to the local network or the Internet.
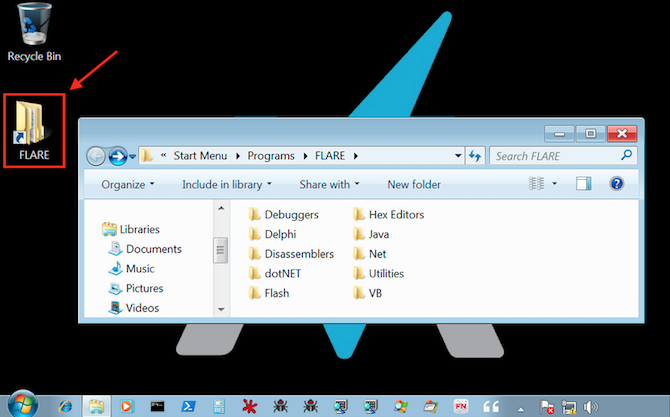
According to FireEye, users can easily customize their FLARE VM installation as it is built using the Chocolatey package management system. Users can choose tools from both the Chocolatey repository and FireEye’s FLARE repository, which is continually expanded.
Ensuring that the tools included in FLARE VM are up to date is also easy. Running the command “cup all” will update all the installed packages.
FireEye has made available usage instructions and source code on GitHub. A blog post published by the company also provides an example for how FLARE VM can be used to analyze a malware sample.
Related: Kaspersky Releases Open Source Digital Forensics Tool
Related: Cisco Releases Open Source Malware Signature Generator
Related: Google’s Binary Comparison Tool “BinDiff” Available for Free












