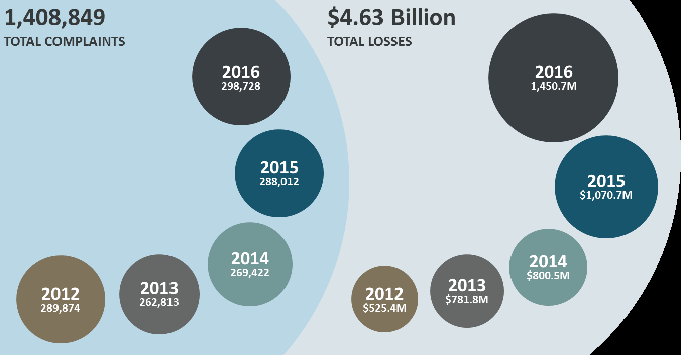
The FBI has published its Internet Crime Report 2016 based on information received by the Internet Crime Complaint Center (IC3). It shows that 298,728 complaints were received by the IC3 during 2016 (up from 288,012 in 2015); and that reported losses to internet crime totaled more than $1.45 billion (up from $1.07 billion in 2015).
These figures, however, are likely to be only a fraction of the full picture. The FBI estimates that only 15 percent of the nation’s fraud victims report their crimes to law enforcement. Nevertheless, by publishing this report, the FBI hopes to help law enforcement recognize and respond to developing trends in internet crime, and to help the public recognize scams before they become victims.
“The 2016 Internet Crime Report,” writes Scott Smith, assistant director, cyber division of the FBI in the report’s introduction, “highlights the IC3’s efforts in monitoring trending scams such as Business Email Compromise (BEC), ransomware, tech support fraud, and extortion.”
He also notes, “This year’s report features a section on the importance of law enforcement collaboration and partnerships with the private sector and Intelligence Community. For example, the FBI continues to expand Operation Wellspring (OWS), an initiative through which state and local law enforcement officers are embedded in, and trained by, FBI cyber task forces and serve as the primary case agents on Internet-facilitated criminal investigations. Overall, OWS task forces opened 37 investigations in 2016 and have worked 73 total investigations since OWS was launched in August 2013.”
The most prolific crimes detailed and analyzed in the report are business email compromise (BEC) and the personal equivalent, email Account compromise (EAC); ransomware; the tech support scam; and extortion.
The BEC scam, notes the report, “began to evolve in 2013 when victims indicated the email accounts of Chief Executive Officers or Chief Financial Officers of targeted businesses were hacked or spoofed, and wire payments were requested to be sent to fraudulent locations.” Since then it has grown and evolved.
“In 2016, the scam evolved to include the compromise of legitimate business email accounts and requests for Personally Identifiable Information (PII) or Wage and Tax Statement (W-2) forms for employees.” Last year, IC3 received 12,005 BEC/EAC complaints, with losses of more than $360 million.
Ransomware often receives greater publicity than BEC, but the instances and losses reported to IC3 are less than BEC losses. “Recent iterations,” says the report, “target specific organizations and their employees, making awareness and training a critical preventative measure. In 2016, the IC3 received 2,673 complaints identified as ransomware with losses of over $2.4 million.
The tech support fraud is surprisingly pervasive and effective. Few people will not have received a tech support cold call; but the ease and speed with which they are detected and dismissed is not consistent across the whole population. “Once the phony tech support company or representative makes verbal contact with the victim, the subject tries to convince the victim to provide remote access to their device. Once the subject has control, additional criminal activity occurs.”
That activity could include demanding a ransom, stealing sensitive personal information, or installing malware. A more recent variation of this fraud convinces the victim to allow access to refund an overpayment for earlier services. “With this access, the subject claims to have ‘mistakenly’ refunded too much money to the victim’s accounts, and requests the victim wire the difference back to the subject company.”
In reality, the fraudster used the provided access to effect the ‘refund’ from a different account belonging to the victim. The victim sees the ‘refund’, doesn’t recognize it as his/her own money, and wires the requested funds to the fraudster.
The volume of money lost to this fraud is not as high as that of BEC or ransomware, but is personal rather than corporate money — and can affect the victims more acutely. “In 2016,” says the report, “the IC3 received 10,850 tech support fraud complaints with losses in excess of $7.8 million.” Noticeably, older victims are often the most vulnerable.
“Extortion,” says the report, “is defined as an incident when a cyber criminal demands something of value from a victim by threatening physical or financial harm or the release of sensitive data.” Noticeably, ransomware (which is clearly a form of extortion) is excluded from this category. It includes DoS, hitman schemes, sextortion, Government impersonation schemes and loan schemes. “In 2016, the IC3 received 17,146 extortion-related complaints with adjusted losses of over $15 million.”















