Network security products are disaggregated into smaller elementary security functions. Compared to a typical network security product, each function is more basic, more stable, simpler to operate and control, more resource efficient, and can be provisioned pervasively, anywhere and per need throughout the network.
Imagine too that there is one security control entity that can select and orchestrate all these disaggregated security functions. This entity can compose new sets of functions, constructing logical information and decision flows between them and thus forming a new security solution – All this without asking or waiting for the security vendor to develop a new feature to protect against a new threat that the product cannot handle right now – a process which can obviously take “forever” until completed (usually the threat ceases to exist long before the solution becomes available).
In order to fight against a new threat or a more violent variant of an existing one (e.g., that has bypassed the current security solution), the security control entity can disaggregate the existing solution and compose the security functions again in a new way, e.g., with new information and work flow rules, to fight against the threat effectively.
The above may seem like a dream, but when we observe the great shifts that the networking arena is going through, we can envision this scenario becoming a reality.
What are the shifts?
Obviously virtualization and cloud architectures are significant ones. However the market is undergoing additional disruptive changes with the advent of Network Function Virtualization (NFV), the disaggregation of the network functions and Software Defined Networking (SDN).
Basically, the SDN concept suggests a centralist control approach that decouples the data-forwarding from the control in network elements, and the NFV suggest how to virtualize and “isolate” basic networking functions, wrapping each function with a set of API’s that would allow easier orchestration of large network environments.
In short, virtualization technologies in general, with the help of SDN and NFV are changing the nature of networks in the sense that networks can become truly dynamic. The main benefits of this are:
• Provisioning of new network application and resources where and when needed.
• Dynamic and “surgical” redirection of traffic flows through network applications per business needs.
• More standard API that wrap the basic network functions, which allow building more vendor agnostic network architectures. This obviously helps to mix & match the best network function for each need, i.e., minimizing “vendor-lock” as much as possible.
• In general, a network that can rapidly adapt its behavior to business needs while reducing its overall cost.
So, how does all this fit into the cyber security arena and to the scenario I described earlier?
I believe that in order to reap the greatest benefit from virtualization, SDN and NFV concepts, the control and data-plane functions of network security devices need to be decoupled. Once this decoupling is done effectively, the data-plane security device can be disaggregated into a software defined set of discrete functions; pretty much the same way it is done with more basic networking elements.
These disaggregated security functions will become, by nature, more pervasive and flexible throughout the network and will be managed by a centralized security control that will enable scenario described in the beginning of the article. Let’s take a look at the following abstract illustrations which can shed some more light on this concept.
Below is a two-step process illustration: first the decoupling of the control layer from the data-plane layer of each security device. Second, the disaggregation of each security device into discrete security functions:
Figure-1: Decoupling the Security Devices
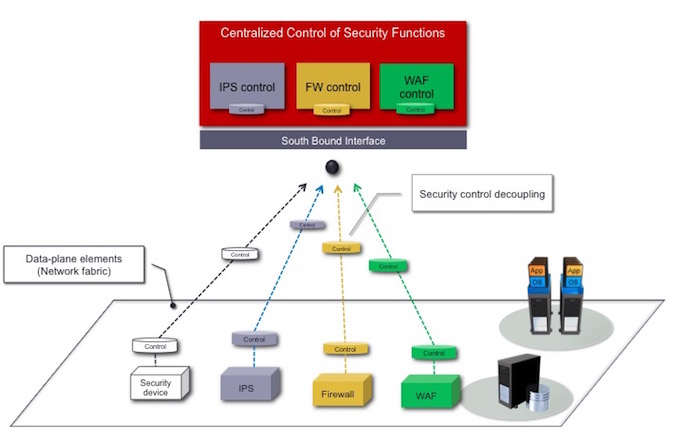
As shown, the control layer was decoupled from each security device and has been positioned in a centralized security control entity.
Its worth mentioning at this stage that in today’s market, each security device has become an “all- in-one” device in a sense that over many years the security vendors have been aggregating a large numbers of security control and data-plane functions into the same network devices with pretty complicated internal flows. This has resulted in products that are complex and resource inefficient.
Take for example the next generation firewall devices (NGFW). Over the years firewalls and their NG versions have been aggregating many security functions such as URL filtering, anti-virus and anti-spam features, intrusion detection features, network behavior analysis and anomaly detection features, application visibility and application access control, anti-DoS protections, , vulnerability scanning, encryption (VPN) and decryption functions ,NAT and more.
This trend of aggregating functions might have seemed like a good idea at the time that the compute and networks were static and non-virtualized, but now with the aforementioned technological and architectural shifts, it’s probably not a good way to go. Let’s see why not:
The idea of the security device disaggregation is illustrated below:
Figure-2: Disaggregated Security Devices
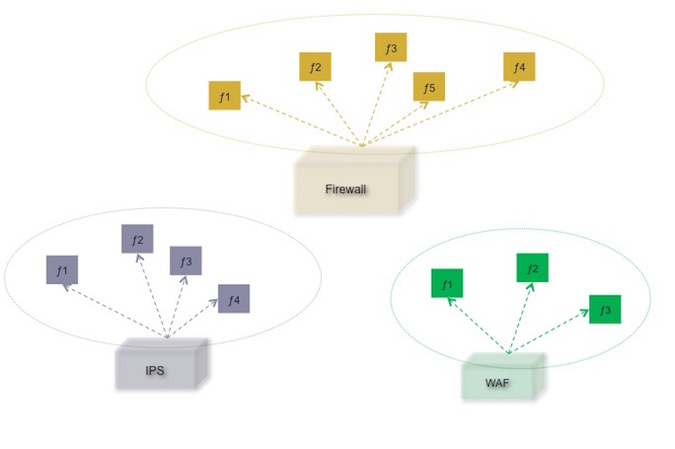
Figure- 3: Orchestrating Disaggregated Security Functions
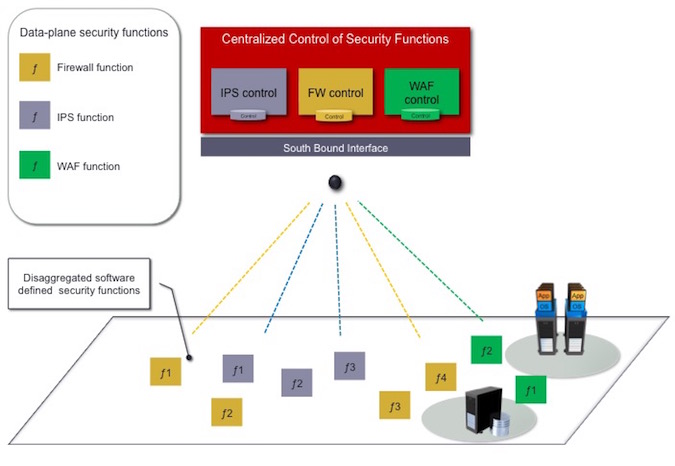
The color of the functions in the Figure above represents a set of security functions that belong to the same security product category, e.g., IPS functions, firewall functions etc. Each security function has its control and data-plane level. The control part is centralized while the data-plan security functions are disaggregated and can be placed, more economically, anywhere in the network per need and per the required resources for the specific “job” they need to perform.
As we imagined at the start, the security controller can orchestrate, e.g., create new compositions of disaggregated security functions together with modified or new logical connections between them – all in order to react quickly against new and evolving security threats.
The above concept represents a new way of approaching large security frameworks, enabling them to be designed, built and managed, and respond much more effectively than they are today.
The concept is pretty abstract but I hope these illustrations speak for themselves and can communicate the tremendous value this approach could potentially bring to the security arena. To summarize the values of the concept:
• Agility & Modularity – disaggregation and composition of a new set of functions becomes a reality and can accelerate the way security systems will reply to evolving threats, fast.
• Quality discrete functions – the aggregation of security functions under the hood of the same product and security vendor has resulted in a compromise on the quality of at least some of the functions. Disaggregation solves this.
• Mix & match – replacing and mixing different data-plane security functions per need will become something that can really happen. This represents a more “democratized” security framework with less vendor lock.
• None or fewer blind spots – security functions can be more easily and economically distributed, pervasively, throughout the entire network, allowing much better visibility and control.
• Stability – each function is more basic and hence more stable.
This entire concept has a very long way to go until it becomes available to the security community, however it seems worth exploring as it can change the balance between the attacker and defender, more in favor of the defenders…















