Organizations are more confident in their ability to detect an OT breach
While the risk to industrial control systems (ICS) and other operational technology (OT) environments continues to be high, organizations are increasingly confident in their ability to detect malicious activity, and only a small percentage of organizations admit suffering a breach, according to a survey conducted by the SANS Institute on behalf of industrial cybersecurity firm Nozomi Networks.
The 2022 OT/ICS Cybersecurity Report (PDF) is based on a survey of 332 individuals representing organizations of all sizes across every continent.
Less than 11% of respondents said they had experienced a cyber intrusion in the last year, down from 15% in 2021, and 24% were confident that their systems were not breached, up from 12% in 2021. Thirty-five percent did not know whether their organization’s systems had been compromised, which is still a significant improvement from the 48% in the previous year.
More than half of respondents said they were confident that they could detect an intrusion within 24 hours and over two-thirds believe they can move from detection to containment within 6-24 hours.
In the previous report, compromised engineering workstations were the sixth most common initial attack vector, being cited by 18% of respondents. However, experts raised concerns at the time about vulnerable engineering workstations and the potential impact associated with compromised devices.
In the past year, the percentage of attacks using engineering workstations as an initial access vector increased to 35%, and this is now the third most common vector, after IT compromises and removable media.
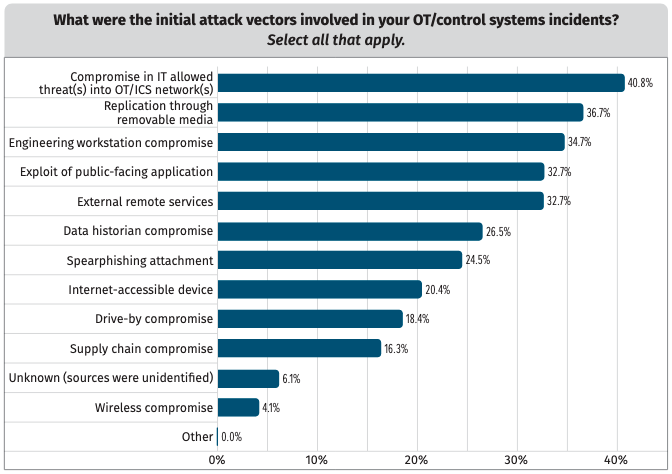
However, it seems many organizations are aware that engineering systems — this includes engineering workstations and instrumentation laptops — are at the greatest risk of getting compromised, followed by operator and server assets running Windows and other commercial operating systems.
“Engineering workstations have control system software that is used to program or change logic controllers and other field device settings or configurations. This critical asset could also be a mobile laptop — essentially a transient device — used for engineering device maintenance that could travel throughout facility sites or elsewhere outside the protection of a segmented plant network,” the report explains.
Learn more about threats to industrial organizations at
SecurityWeek’s ICS Cyber Security Conference
Ransomware remains the top concern, which is not surprising given that industrial organizations are targeted by many cybercrime groups. Roughly the same percentage of respondents are also concerned about state-sponsored cyberattacks, closely followed by non-state attacks (hacktivism and cybercrime other than ransomware), and supply chain and third-party risks.
The number of respondents that reported having a bigger ICS/OT cybersecurity budget increased significantly compared to the previous year and nearly all organizations are now conducting security audits, monitoring OT security, and investing in training and certification.
Related: Weaponized PLCs Can Hack Engineering Workstations in Attacks on Industrial Orgs
Related: Hackers Can Use Rogue Engineering Stations to Target Siemens PLCs
Related: Flaws in Rockwell Automation Product Expose Engineering Workstations to Attacks












