Organizations that use industrial control systems (ICS) and other operational technology (OT) are increasingly concerned about cyber threats, and while they have taken steps to address risks, many don’t know if they have suffered a breach, according to a survey conducted by the SANS Institute on behalf of industrial cybersecurity firm Nozomi Networks.
The SANS 2021 OT/ICS Cybersecurity Report is based on information provided by 480 individuals from a wide range of industries.
The survey conducted by SANS showed that nearly 70% of respondents believe the risk to their OT environment is high or severe, which is a significant increase from the 51% in 2019, when SANS conducted a similar survey.
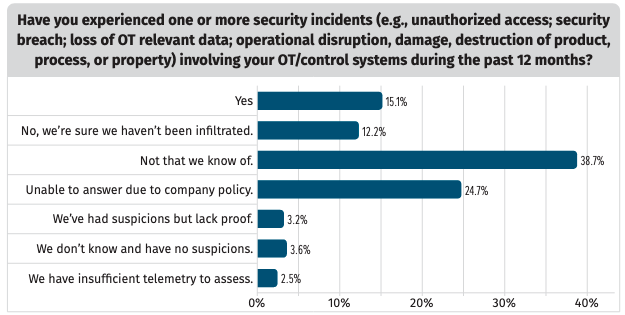
While many organizations are concerned about cyber threats to their OT environments, SANS found that 48% of respondents don’t know whether they have experienced a security breach involving OT or control systems in the past year, an increase from the 42% that gave the same response in 2019. This indicates a need for organizations to improve their detection and response capabilities.
Only 12% are confident their systems have not been compromised, and 15% have admitted detecting security incidents, many of which caused some form of disruption to operations.
A majority of respondents blamed incidents on “hackers,” followed by organized crime, service providers and contractors, employees, activists, and state-sponsored threat actors.
When it comes to initial attack vectors involved in the incidents they have experienced, the top answer was external remote services (36%), followed by exploitation of public-facing applications (32%), internet-accessible devices (28%), spear phishing (26%), removable media (24%), and compromised engineering workstations (18%).
“Of particular concern is the 18% of initial vectors leveraging the engineering workstation,” the authors of the report noted. “This percentage raises some concern because engineering workstations represent key terrain to accomplish a variety of effects in stage 2 of the ICS Cyber Kill Chain and could have contributed to the high numbers of incidents with impact on processes.”
Stage 2 of the ICS Cyber Kill Chain refers to the development and execution of an attack using knowledge acquired in the first stage.
Learn more about OT security at SecurityWeek’s ICS Cyber Security Conference and SecurityWeek’s Security Summits virtual event series
More than 50% of respondents named engineering systems as posing the greatest risk for getting compromised.
As for the steps they have taken over the past years to improve their OT security posture, nearly half of organizations have increased their ICS security budget, and more than two-thirds now have a security monitoring program in place.
More than half claim they are now able to detect an incident within 24 hours, up from 34% in 2019.
In terms of cloud adoption, while only 1% of respondents said they use cloud-based services for OT or ICS systems, nearly all are using cloud technologies to directly support industrial operations.
Related: Over 90% of OT Organizations Experienced Cyber Incidents in Past Year: Report
Related: Survey: 1 in 4 Facility Managers Experienced OT System Breaches
















