A high severity vulnerability revealed last week that affects HTTPS and other services that rely on SSL and TLS has not been patched by most affected cloud services, according to a recent scan.
To demonstrate the impact of this security issue, a team of researchers published a paper (PDF) on a cross-protocol attack method that involves the old SSLv2 protocol still supported by many servers.
Dubbed DROWN (Decrypting RSA with Obsolete and Weakened eNcryption), the attack allows potential adversaries to crack encrypted communications and steal potentially sensitive data.
DROWN provides attackers with the ability to compromise an encrypted session even if the session is encrypted with the newer and more secure TLS protocol. As a result, attackers can intercept encrypted traffic, impersonate a trusted cloud provider, and also modify traffic to and from the service.
“DROWN shows that merely supporting SSLv2 is a threat to modern servers and clients,” the security researchers explained. “It allows an attacker to decrypt modern TLS connections between up-to-date clients and servers by sending probes to a server that supports SSLv2 and uses the same private key.”
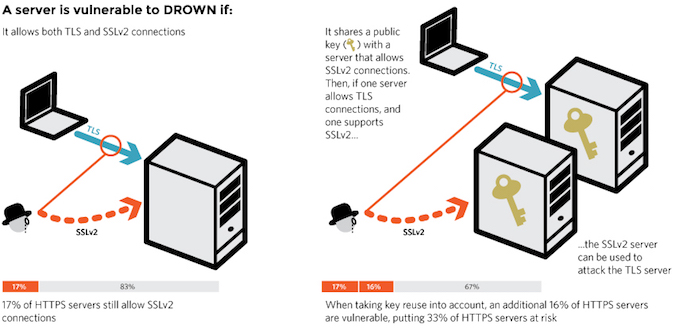
Last week, the OpenSSL Project released updates to resolve several vulnerabilities in the crypto library, including CVE-2016-0800, a high severity flaw said to affect a quarter of the top one million HTTPS domains (overall, over 2.3 million HTTPS servers are vulnerable), as well as one-third of all HTTPS websites.
One week after the high severity flaw was discovered, 620 out of 653 cloud services were found to be still vulnerable to compromise, Skyhigh Cloud Security Labs’ Sekhar Sarukkai notes in a blog post. The report shows that cloud providers have been slow to respond to DROWN, although they acted faster when SSL vulnerabilities such as Heartbleed and POODLE were discovered.
With the average organization using 56 vulnerable services and with 98.9 percent of enterprises using at least one vulnerable service, this lack of reaction doesn’t spell good news, Sarukkai says. The vulnerability affects all cloud providers that still support SSLv2 or use a private key shared with a server that supports SSLv2.
Previously, cloud providers reacted more promptly when similar critical vulnerabilities were revealed, with 92.7 percent of the affected cloud providers having patched their systems to close the Heartbleed vulnerabilities within the first week. In the case of DROWN, only 5.1 percent of vulnerable cloud providers have performed necessary remediation within the first week.
Last year, security firm Venafi revealed that one year after the famous Heartbleed OpenSSL vulnerability (CVE-2014-0160) was disclosed, 74 percent of Global 2000 organizations still hadn’t completely remediate the risks.















