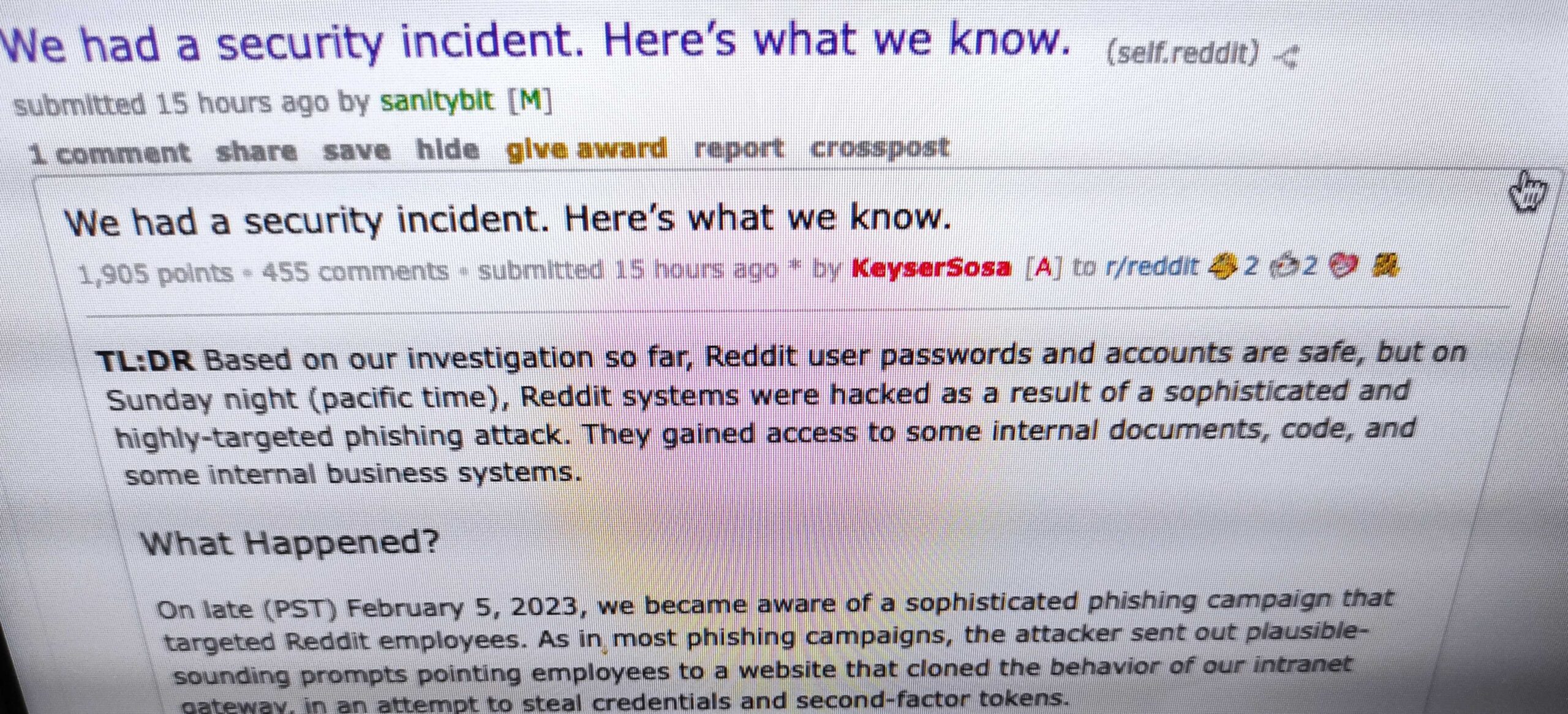
Reddit on Thursday informed users that its systems were hacked as a result of what the company described as a sophisticated and highly targeted phishing attack aimed at employees.
According to Reddit, the intrusion was detected on February 5. The hackers gained access to some internal documents, source code, internal dashboards and business systems.
Up until this point in the investigation, Reddit has determined that the exposed information includes limited contact information for hundreds of contacts and current and former employees, as well as some advertiser information.
“Based on several days of initial investigation by security, engineering, and data science (and friends!), we have no evidence to suggest that any of your non-public data has been accessed, or that Reddit’s information has been published or distributed online,” Reddit said.
There is no indication that user passwords or accounts have been compromised. The company also said there is no evidence of a breach of production systems, where the platform runs and where a majority of its data is stored.
The data breach was discovered after an employee informed Reddit’s security team that they had fallen for a phishing attack. The attackers targeted Reddit employees with “plausible-sounding prompts” that led them to a phishing website mimicking its intranet gateway.
A Reddit representative noted in an AMA (Ask Me Anything) thread that the employee whose credentials were phished did have two-factor authentication (2FA) enabled on their account, as the company requires it for all employees.
However, it seems that the phishing page targeted not only employee credentials, but also their second-factor tokens.
Several major tech companies were targeted in sophisticated phishing attacks in the past months. One of them is Zendesk, which revealed recently that some employees handed over their credentials to threat actors in the fall of 2022.
At around the same time, companies such as Twilio, Cloudflare and at least 130 others were targeted in a phishing campaign dubbed 0ktapus, which appeared to be the work of financially-motivated threat actors.
Related: Reddit Names Allison Miller as CISO, VP of Trust
Related: Accounts of Reddit Moderators Hijacked in Pro-Trump Hack
Related: Reddit Locks Down Accounts Due to ‘Security Concern’